A new form of cyber attacks has been discovered, leveraging information about current state of an application’s interface and leading to compromise of sensitive information, such as log in credentials.
Called UI state inference, the attack was demonstrated by security researchers on the Android platform, at the USENIX Security Symposium in San Diego, on Friday.
However, they say that it should be possible to be deployed on other operating systems such as Mac OS X, iOS, and Windows.
“After evolving for decades, the most recent design is called compositing window manager, which is used virtually in all modern Oses,” write the researchers in the paper titled “Peeking into Your App without Actually Seeing It: UI State Inference and Novel Android Attacks.”
This is a general side-channel attack that targets exposing the running UI state of an app at window level as it relies on the shared-memory mechanism used by window managers for displaying application windows on the screen.
“This side channel exists because shared memory is commonly adopted by window managers to efficiently receive window changes or updates from running applications,” researchers say.
Worth mentioning for this type of attack is that the malicious app, which should run in the background, does not need any special permissions, Internet connectivity being sufficient.
Determining the UI state can be done with a certain degree of accuracy, which differs from an app to another.
In their demonstration, the researchers managed to steal the log in credentials of several popular apps on Android, the average success rate for determining the UI state being between 82% and 92% for some candidates; this increases to more than 91% with some popular applications and even 93% with others.
In the case of Gmail, the UI state detection was accurate in 92% of the cases, while inferring, whereas with Amazon the accuracy was low, at 47.6%, because certain features were not sufficiently clear for the inference method used by the researchers.
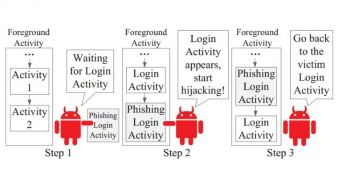
With information on the current interface accessed by the user, attackers could devise a method for injecting a phishing activity in the foreground, making the user believe that they’re signing into the desired service but instead offering the credentials to the cybercriminals.
Apart from collecting credentials, the researchers were also able to access sensitive images taken with the built-in phone camera.
During their tests, the researchers used Samsung Galaxy S3 devices, running Android 4.1 for most experiments.
 14 DAY TRIAL //
14 DAY TRIAL //