A new string of malware with instructions to steal credentials from any website accessed by the victim deploys destructive routines on the computer if it does not evade analysis tools included in antivirus products.
If the threat does not destroy the computer during the installation procedure, it injects itself into the process of Internet Explorer, Chrome or Firefox, and captures user input on almost any web page.
The data is collected before it is encrypted by the web browser and it is delivered to the command and control (C&C) server via HTTP.
Anti-analysis function comes with dire consequences
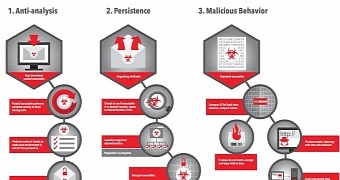
Malware analysts at Cisco Systems' Talos Group caught a sample of the threat, which they called Rombertik, and reverse-engineered it to determine the functions it integrates for dodging both static and dynamic analysis.
One of the final checks Rombertik performs to make sure it escapes detection involves creating in the memory of the system a hash of one of its resources and comparing it to the unpacked version.
A difference in the compilation times unleashes destructive behavior, and one course is to damage the master boot record (MBR) of the compromised computer and make the system inoperable; if access to the MBR is not possible, it starts encrypting the files in the user’s home folder.
The MBR is a boot sector positioned at the beginning of a hard drive, and it is responsible for maintaining information about all the partitions present on the computer and the data they hold.
If Rombertik overwrites the MBR, the computer enters a continuous restart loop and displays the message “Carbon crack attempt, failed.”
The researchers say that the bytes containing information about disk partitions are replaced with null bytes, which makes recovery of the data a much difficult process.
The encryption process is also damaging, as the malware processes the files individually and locks them with a randomly generated RC4 key.
“While Talos has observed anti-analysis and anti-debugging techniques in malware samples in the past, Rombertik is unique in that it actively attempts to destroy the computer if it detects certain attributes associated with malware analysis,” Ben Baker and Alex Chiu from Talos wrote in a blog post on Monday.
Malicious package includes mostly non-threatening code
The analysis of the malware revealed that its authors tried to obfuscate the sample by adding garbage code in the packed version. They say that more than 97% of the code in the packed version served no malicious purpose and included 75 images and over 8,000 functions that were never used.
Also interesting is the technique used by Rombertik before unpacking to trick sandbox tools in antivirus products. The threat would delay its execution by writing a random byte in the memory of the system 960 million times.
One consequence of this would be that the sandbox would time out waiting for malicious behavior to occur. However, this action would also flood application tracing tools, as recording the activity would create a 100GB-large log and would require more than 25 minutes to write it on the disk.
 14 DAY TRIAL //
14 DAY TRIAL //