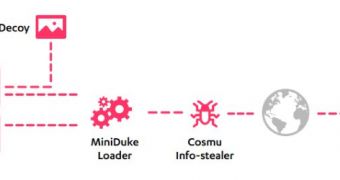
Security researchers identified a new persistent threat born from a combination of components particular to Cosmu and MiniDuke malware families.
Because the analyzed samples integrated a loader related to the one used by MiniDuke and a payload very similar to what Cosmu employed, F-Secure decided to name it CosmicDuke.
The malware features data collection components that include keylogging, stealing clipboard content, taking screenshots and stealing passwords from popular chat and email clients, as well as web browsers. It also looks after Windows password hashes, PKI certificates and associated private keys and WLAN passcodes.
According to F-Secure, the keylogging activity is suppressed if certain antivirus processes are active on the affected system.
All the information is sent to a remote server via FTP or WebDav servers, which are also used for updating the malware components.
The IP addresses CosmicDuke connects to are mostly from Europe (Greece, Poland, Czech Republic, Germany, Romania, Russia, United Kingdom, Sweden, Luxembourg and Netherlands), but the researchers also found a sample group that connects to an address in the U.S.; most servers were still alive when the analysis was published.
According to F-Secure, “the filenames and content used in CosmicDuke's attack files to lure victims contain references to the countries of Ukraine, Poland, Turkey, and Russia, either generally in use of language or included detail, or in allusions to events or institutions. The filenames and content chosen seem to be tailored to their target’s interests, though we have no further information on the identity or location of these victims yet.”
In some cases the targets are tricked into opening a PDF file containing an exploit (CVE-2011-0611) or an executable masked as an image or document file.
In one example, the security experts found an image that had not been stripped of EXIF metadata, offering information about the date the picture was taken and the phone model that was used. The picture was for a receipt payment and the language was Russian.
It appears that the authors of CosmicDuke masked the fact that the malicious file was an executable by using the Right-to-Left Override (RLO) feature in Windows.
The technique allows the file to appear as a harmless item, and even if the file manager in Windows is configured to show the file extension, the item is still cloaked. The only hint that the file is something else than it pretends to be is to check the file type column, which reveals its true nature. However, most users rarely glance at this area.
 14 DAY TRIAL //
14 DAY TRIAL //