A few days ago, the world learned of the existence of the first ever Android spam botnet. However, Google, along with other security firms, argue that this isn’t actually an Android botnet.
The situation has become somewhat controversial, with a number of security solutions providers rolling up their sleeves to find out more about the alleged botnet.
So, here’s what they’ve found.
Google representatives have stated that there is no evidence to support the researchers’ findings.
“Our analysis suggests that spammers are using infected computers and a fake mobile signature to try to bypass anti-spam mechanisms in the email platform they're using,” they said.
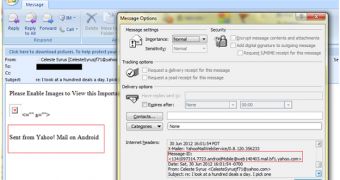
Symantec has also has studied these spam messages and agrees that the “Sent from Yahoo! Mail on Android” signature and the “androidMobile” string in the Message-ID field indicate that the messages could come from a compromised Android mail client.
However, they believe that they don’t appear to originate from a malicious Android app that sends emails through compromised Yahoo! accounts.
“First, without a local exploit and specially crafted hijacking code, applications that attempt to send mail through the default Android mail application cannot do so automatically in the background,” Symantec experts said.
“The mail client will, at most, display the message to be sent and require the user to actively send the message. Further, the mails do not appear to come from the default mail client, but rather specifically, the Yahoo! Mail for Android application.”
Furthermore, they reveal that the email accounts from which the spam is sent don’t appear to be legitimate. Instead, they seem to be specially created to send these messages.
They claim that there are a number of possible scenarios, but the most likely one is that the spammers are utilizing the same web services used by the Yahoo! Mail app for Android. This means that they’re either sent from compromised PCs or through malicious Android software.
On the other hand, Lookout, the mobile security firm, states that the Message-ID and the footer can be forged.
Moreover, the company has identified a number of issues in the Yahoo! Mail Android app that could have “potentially broader implications” for users.
Terry Zink of Microsoft, and one of the first to report on the Android botnet, published another post, admitting that it might be possible that the spam is actually sent from PCs.
“Yes, it’s entirely possible that bot on a compromised PC connected to Yahoo Mail, inserted the the message-ID thus overriding Yahoo’s own Message-IDs and added the “Yahoo Mail for Android” tagline at the bottom of the message all in an elaborate deception to make it look like the spam was coming from Android devices,” he wrote.
On the other hand, he still believes that there may be a chance that “Android malware has become more prevalent” and this is in fact an Android spam botnet.
Sophos’ Chester Wisniewski has also provided more information after further analyzing the situation. The researcher admits that they haven’t actually obtained a malware sample, but he claims that evidence suggests that it exists.
He highlights the fact that the company’s research hasn’t found any evidence of forgery.
“The messages are delivered to our spam traps from genuine Yahoo! servers with valid DKIM signatures. The Yahoo! headers note the origin of the messages as "Web API" which could indicate either the normal Yahoo! webmail interface or, as we believe, the Android API interface referenced in the mail headers,” he explained.
“The Message-IDs are all valid for the Yahoo! mailers sending them as well. It would not be possible to spoof this information externally.”
Yahoo! has also launched an investigation to determine if its Android application has something to do with it.
 14 DAY TRIAL //
14 DAY TRIAL //