Office workers are advised to be on the lookout for emails that appear to carry a confidential message to all employees. Experts say that these notifications are designed to spread a piece of malware capable of stealing user passwords.
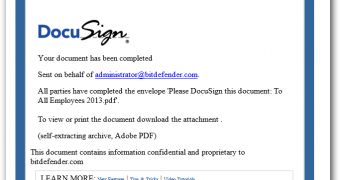
Entitled “To all Employees – Confidential Message,” the bogus emails appear to have been sent via DocuSign. In reality, they're not sent via DocuSign, but the sender has spoofed the email address to make it look like they are.
Recipients are informed that their “document has been completed,” and they’re urged to download the attached file named “Please DocuSign this document: To All Employees 2013.pdf.”
To make everything more legitimate-looking, the cybercriminals have even added: “This document contains information confidential and proprietary to [company name].”
Bitdefender experts have analyzed this spam campaign and they’ve found that the document is actually a password stealer that’s designed to collect passwords from email clients and the ones saved by web browsers for various websites.
The malicious element also collects data on servers, port numbers, FTP clients, and cloud storage applications.
Once the information is harvested, the malware – detected as Trojan.Generic.KD.834485 – sends it back to the attacker.
In addition, the Trojan also attempts to log into other machines from the network via the remote desktop protocol by trying various weak passwords such as “123456,” “password” or “iloveyou.”
In some cases, the threat also downloads other pieces of malware, including the notorious ZeuS, which specialized in stealing online banking-related information.
To protect themselves against such threats, users are advised to double-check the legitimacy of an email before opening the attachments it carries. In such cases, opening a single attachment could have devastating effects for an organization.
If proper security checks are not set in place, the attackers could gain access to the entire network.
Update. The article has been updated to clarify that the malicious emails are not actually sent via DocuSign. Instead, their layout and the sender's email address are forged to make it look as if they are.
 14 DAY TRIAL //
14 DAY TRIAL //