Some of the modules used in cyber-espionage toolkit Regin are likely to have been created before the malware platform and integrated into it as they were readily available.
Security researchers from Kaspersky analyzed Hopscotch and Legspin components discovered in Regin advanced persistent threat (APT) and determined that they could have been used separately for lateral movement and as a backdoor into systems targeted in other attacks.
Simple tool for lateral movement
According to the analysis from Costin Raiu and Igor Soumenkov, Hopscotch is an interactive tool that permits moving deeper into the targeted network. It does not contain any exploits but includes an executable file for lateral movement activity.
The tool relies on authentication credentials provided by the attacker in order to access remote machines in the network and establish a foothold.
“The module can use two routines to authenticate itself at the target machine: either connecting to the standard share named ‘IPC$’ (method called ‘NET USE’) or logging on as a local user (‘SU’ or ‘switch user’) who has enough rights to proceed with further actions,” the researchers say in a blog post.
Once authenticated, the binary in Hopscotch launches on the remote machine a payload (SVCSTAT) executable from its resources by creating a new service called Service Control Manager. The interesting part is that the service runs for only one second, enough to launch the payload, and then it is stopped and deleted.
SVCSTAT is required for communication with the binary over encrypted channels, allowing the operator to deliver other malicious tools on the remote machine.
Administration tool with large list of commands
Regin’s Legspin module is also designed for computer administration purposes, permitting remote access to a compromised system.
The researchers found evidence that it was compiled in 2003, although there are indications that it has other versions that have been used before.
It comes with a hefty list of commands for administrative operations, some of them offering a description of the parameters it supports.
The version of Legspin analyzed by Kaspersky allows file management on the infected computer, retrieving data, checking item timestamps, accessing system information and storage space available, dumping registry info, and listing visible servers in a domain or the domain controllers.
Running commands, managing processes, logging in as a different user, initiating brute-force attacks on remote shares, and creating, modifying and deleting system services are also on the list of options provided by Legspin.
The two researchers draw attention to the fact that the details currently available for Regin may already be old news and that the threat actor is probably relying on new modules and attack methods.
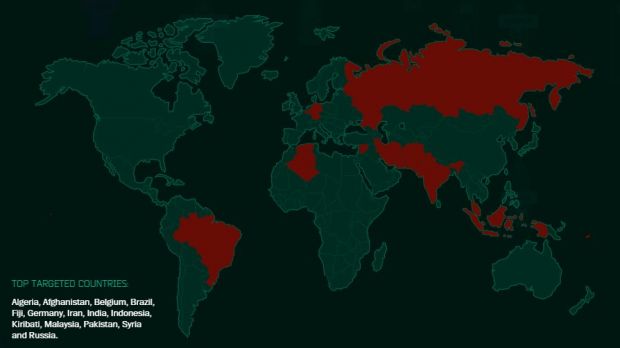
Although its analysis began when it was discovered in 2012, there are still plenty of unanswered questions regarding Regin. The conclusion at the moment is that it is used for cyber-espionage purposes and it can compromise and monitor GSM networks.
Its targets range from telecommunication companies, government organizations and political entities to financial institutions, academia (research) and specific individuals.
 14 DAY TRIAL //
14 DAY TRIAL //