A tool for reversing the encryption process of CoinVault crypto-malware is currently available for download, with new decryption keys being added as the investigation advances.
CoinVault emerged in mid-November 2014 and it was the first malware of this kind to offer its victims the possibility of recovering some of the encrypted data, in an effort to show a sign of good faith and thus increase the amount of ransoms paid.
Database with decryption keys obtained from C&C server
The National High Tech Crime Unit (NHTCU) of the police in Netherlands managed to access a command and control (C&C) server and retrieve a database containing initialisation vectors (IVs), keys and wallets for digital currency used by CoinVault operators.
The law enforcement organization contacted security researchers from Kaspersky, who managed to come up with a tool that can unlock files scrambled by CoinVault.
This means that users whose data has been encrypted by this piece of ransomware have a chance of getting it back without paying the ransom.
Memory dumps speed up writing of decryption tool
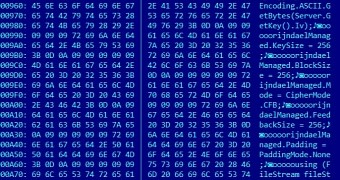
In a blog post on Monday, the researchers explained that, in order to create the decryption tool, they needed to determine the encryption algorithm and the block cipher mode used.
Based on previous information gathered from analyzing the malware, the experts were able to skip some steps towards achieving their goal, avoiding reverse engineering activity, which is a more time-consuming process.
The method used consisted of running the malware in a virtual environment and tracing its activity, as well as retrieving information from memory.
“We knew from the previous CoinVault samples that the malware was using the RijndaelManaged class, so all we had to do was search in the memory dump for this string,” Jornt van der Wiel and Santiago Pontiroli said.
After finding out that AES was still used by that particular variant, they were able to produce the unlock tool.
However, before running the decryption program, users are advised to check on a specially created website if the files can be retrieved.
 14 DAY TRIAL //
14 DAY TRIAL //