The creators of the CoinVault ransomware with file encryption capabilities have come up with a replacement, changing the name to BitCryptor and the UI for the ransom message to reflect the new malware.
However, apart from this, the method of infection and the encryption routine of the threat remain the same.
Shadow copies are deleted
The move is probably the result of Kaspersky releasing last month a decryption tool for CoinVault, which allows victims to recover their data without paying the cybercriminals for the decryption key.
The tool was created after the National High Tech Crime Unit (NHTCU) of the police in Netherlands gained control over an active command and control server used by the crooks, which stored a database with different decryption keys.
According to the analysis from Bleeping Computer, “BitCryptor is essentially the same exact infection as CoinVault.”
Once deployed on a system, the crypto-malware deletes all backup copies created automatically by Windows’ Volume Snapshot Service (VSS), and then proceeds to encrypt files of interest to the victim, forcing them to pay the ransom.
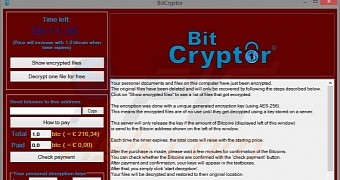
The message alerting of the illegal data encryption says that the algorithm used for the job is AES and the key used is a 256-bit one, stored on the server controlled by the attackers.
Popular files receive encryption treatment
BitCryptor makes sure to avoid data essential for running the system and skips items in folders such as Program Files, AppData, ProgramData, Boot, Windows, WinNT, Recycle.bin, Downloads, All Users, or temporary locations.
Instead, it focuses on items with extensions for documents, media files (audio, video and images), databases or archives, which are highly likely to hold information of significance to the victim.
The fee for getting the data back is currently 1 bitcoin ($237 / €208), which may be paid in a specific period, a counter in the ransom message informing of the amount of time left.
The destination wallet for the money is also provided. Bleeping Computer reports that, at the moment, there is no way to unlock the files for free.
The evaluation of the malware also revealed that some processes belonging to security products (Malwarebytes, SpyHunter, RogueKiller, Silent Hunter) or software could prevent it from running its routines.
 14 DAY TRIAL //
14 DAY TRIAL //