In September 2013, researchers revealed that the ZeroAccess and TDSS botnets shared parts of their command and control infrastructure. The result of this is that Microsoft’s disruption of ZeroAccess also impacted TDSS.
According to Trend Micro, the botnets shared part of their C&C infrastructure for click fraud operations. Since Microsoft targeted ZeroAccess’s click fraud component, the takedown efforts also impacted the TDSS botnet.
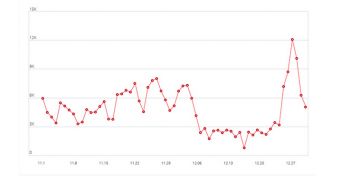
However, the effects on TDSS were only temporary since the botnet’s click fraud side picked up just before 2013 ended. Furthermore, the number of TDSS infections and the threat’s communications have not been impacted by the disruption of ZeroAccess.
Experts say the two botnets might have exchanged URL lists for click fraud operations to help each other generate a bigger profit. Furthermore, some TDSS malware versions appear to be using the old ZeroAccess domain generation algorithm (DGA) module.
 14 DAY TRIAL //
14 DAY TRIAL //