Swiss iPhone developer Nicolas Seriot has presented his talk on iPhone Privacy (from Geneva) in PDF format showing to the world how a malicious application can harvest personal data on non-jailbroken iPhones just as well. There is no need for the developer of such an app to use private APIs while areas like email accounts, the keyboard cache content and the WiFi connection logs are fully accessible.
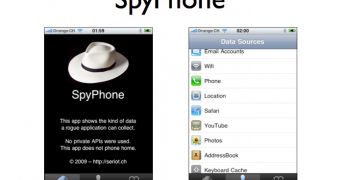
The developer in question has created a proof-of-concept app called SpyPhone. It aims to demonstrate how Apple’s API open to developers can be also used to read or edit a user’s address book, and even have a glance at a user’s web-browsing habits, which would “certainly interest marketers, spammers, thieves, competitors and law enforcement officials,” Seriot says.
“For a few months, there have been several reports about iPhone privacy issues in non-tech press [...] November has been rich in iPhone privacy reports in main press. Four different worms have been infecting jailbroken iPhones [...] In California, iPhone app editor Storm8 is targeted by a federal lawsuite [sic] because its applications harvest users cell numbers,” he writes, enumerating the respective worms.
1. Ikee (Rick Astley) – changes wallpaper, 21 yrs Australian, got hired; 2. Holland 5€ ransom – locks iPhone against a ransom; 3. IPhone/Privacy.A – steals iPhone content, invisible; 4. Duh / Ikee.B – steals iPhone content, changes root password, Lituanian botnet.
Seriot then goes to show off SpyPhone, which he describes as “an application intented [sic] to show the kind of data a rogue application can collect.” According to the developer, that includes Safari / YouTube Searches, Phone and Email accounts, Contacts, Keyboard Cache, Geotagged Photos Location, and even GPS and Wifi Location, which are also logged by the iPhone OS. He notes that Apple's reviewers might be fooled by hackers who delayed the activation of their spyware. Payload encryption might also be used to hide the behavior of malicious code, according to Seriot.
 14 DAY TRIAL //
14 DAY TRIAL //