Security is one of Chrome's big features, one that Google likes to brag about. For good reason too, Chrome, while not impenetrable, has remained mostly problem free, there have been few known Chrome bugs exploited in the wild, if any.
A large part of this is possible thanks to the sandbox on which Chrome was built from the beginning. The idea is that everything Chrome does is kept separate from the machine and the operating system it's running on as much as possible.
Web content can't access anything outside of Chrome directly and the other way around, apps can't mess with Chrome's internal processes or the operation of web pages and apps.
The sandbox itself is very hard to break. There have been only a few documented ways of doing this, by using a long string of bugs in Chrome itself. These vulnerabilities were discovered by security experts as part of the Pwnium competition.
With the sandbox hard to break in a direct attack, malicious websites or code will try to find cracks in other parts of the system, which they can then use to bypass the sandbox.
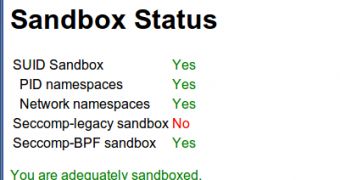
To prevent this, Chrome is now using a new feature in the Linux kernel, seccomp-bpf, which restricts the Chrome renderer processes can do.
Specifically, Chrome now uses a whitelist of sorts to define what system calls the renderer process is allowed to do, just the ones that it needs for normal operations. Any other request is ignored outright.
This means that malicious code or simply poorly written apps won't be able to make calls they're not supposed to and which they don't need for what they're supposed to do.
"A simple example: if we know that Chrome renderers don’t need a system call such as vmsplice, or a facility such as 'inotify,' we can just deny them completely. We use a broker process model to keep the list of allowed system calls small," Google's Julien Tinnes wrote. "Installing this filter in the kernel improves the security of our users."
Since this is a built-in feature in the Linux kernel, any distro that uses a recent kernel version with seccomp-bpf enabled will be able to make use of it.
But for Google, more important is the fact that this feature is now available for Chrome OS, which uses a stripped down Linux kernel at its core. Needless to say, this won't be available for Windows or Mac OS.
Chromebooks were already quite safe and almost immune to most security problems plaguing computers, this improvement should make them even safer.
 14 DAY TRIAL //
14 DAY TRIAL //