A highly organized cybercriminal group in China has been constantly stealing from bank customers in South Korea using Android apps since 2013.
Dubbed the Yanbian Gang after the Prefecture in Jilin with the same name, the group has been attributed the creation of almost a thousand fake versions of Google Play app, which comes pre-installed on Android devices.
Fake banking app replaces the original
The distribution of the malicious applications is done through links in mobile text messages (smishing - SMS phishing) or by getting them downloaded by other malware planted on the victims’ devices.
Security researchers at Trend Micro, who have been tracking the activity of the group for a long time, say that none of the compromising apps was available for download from Google’s official marketplace or any other third-party app store.
The gang operates by delivering the victim a fake banking app that mimics the icon and user interface of the original solutions. To make sure that the malicious resource is used, a routine has been included to remove legitimate app from the device.
According to the researchers, the fake app executes when certain conditions are met, such as rebooting the phone, receiving a text message or modification of the network configuration.
When running, the malicious services work in the background continuously extracting information, such as bank account numbers, usernames, passwords and personally identifiable information (PII).
Five South Korean banks targeted, at least 4,000 users defrauded
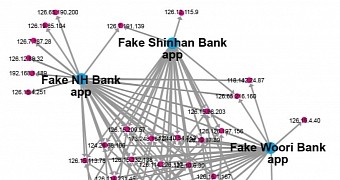
As per Trend Micro's findings, the cybercriminals rely on an infrastructure with 38 command and control (C&C) servers in different countries. 26 of them were contacted by at least two malware samples.
Simon Huang, mobile threat researcher at Trend Micro, says that among the banks targeted by the Yanbian Gang are KB Kookmin Bank, NH Bank, Hana Bank, Shinhan Bank, and Woori Bank.
Huang says that during the September 2013 - April 2014 timeframe the hackers were able to steal from the bank accounts of 4,000 South Koreans, with fraudulent transactions of up to $1,600 / €1,400 being executed on a daily basis.
Four gang member categories have been distinguished during the research: the organizer - who recruits the other members, the translators - who localize the threats, the cowboys – in charge of collecting the money from the attacks and delivering it to the organizer, and the malware authors - who are hired to develop the malicious apps and receive a monthly salary. They all communicate with the organizer and may not know each other.
Deploying the SMS phishing campaign may have been carried out through GSM modems that can send thousands of messages per hour, Huang says.
 14 DAY TRIAL //
14 DAY TRIAL //