Cyber-crooks are exploiting the major earthquake that occurred in Chile on Saturday by poisoning search results related to the event in order to push scareware. Security researchers warn that a new technique is being used to erroneously display the file format for malicious links as PDF.
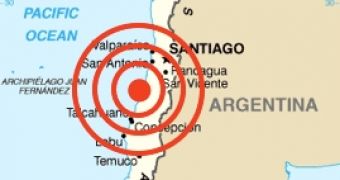
An 8.8 magnitude earthquake struck the coast of Chile on February 27, 2010 at about 03:30 local time, only 115 km away from the country's largest city, Concepción. Buildings collapsed and the infrastructure was badly damaged in several cities in the area, including the country's capital, Santiago.
A series of strong aftershocks of magnitudes of over 6 and 5 were recorded and a separate 6.9-magnitude offshore earthquake was recorded as well, causing tsunami alerts to be issued in 53 countries. The official death toll so far is 708 people and the damages are estimated at over $15 billion.
As with any event of global significance that generates a fair amount of Internet search engine traffic, cyber-crooks have begun exploiting the recent catastrophe for their own benefit. Security researchers from Web security vendor Websense warn of on-going black hat search engine optimization (BHSEO) campaigns poisoning the search results for Chile earthquake-related queries.
Search keywords including tsunami and Hawaii, one of the countries most at risk of being affected by the phenomenon in the aftermath of the quake, have also been littered with links to scareware-pushing websites. However, unlike similar recent attacks, the experts have observed a new technique being employed, which is likely to increase this campaign's success rate.
"Usually the links in the search results look like ordinary links pointing to regular web pages. This time the bad guys have changed tactics to make their search results look even more convincing, by tricking Google into thinking it's a PDF file. […] That's not true, it is in fact a regular HTML page that when visited will redirect the user to […] just another rogue AV fake scanning page," Websense warns.
Another interesting aspect that has been observed is the use of .IN (India) TLD domain names in this campaign. This is actually consistent with a significant increase in the number of .IN domains used in recent scareware-related schemes. On Saturday, we reported about virus-total.in (don't visit), a domain named after the popular VirusTotal file scanning service, being used to distribute similar malicious applications.
 14 DAY TRIAL //
14 DAY TRIAL //