Following recently published documents about CIA’s endeavor to create a malicious version of Xcode, the development tool provided by Apple, a security researcher offers developers instructions on how to verify if they use a genuine instance of the utility or not.
According to information from The Intercept, the tampered Xcode edition would allow the spying agency malware injection capabilities in software (for both the desktop and the mobile platform) built with it.
Apart from creating backdoors in the programs, the poisoned Xcode could be used to disable prompt screens when exporting the developer’s code signing keys, thus allowing signing and injecting malicious code in the app, and distributing through Apple’s official channels.
Exporting developer keys pops security alert
On Tuesday, iOS security expert Jonathan Zdziarski compiled a set of useful instructions for testing Xcode’s integrity.
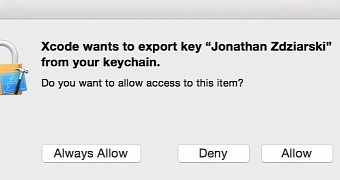
The effort starts by investigating if the security mechanisms in the tool work as intended by Apple; one detail offered in the document from The Intercept about Xcode refers to changing the behavior of the “securityd” daemon so that the developer is no longer alerted when the signature keys are exfiltrated.
“A good litmus test to see if securityd has been compromised in this way is to attempt to export your own developer keys and see if you are prompted for permission,” he says in a blog post.
If no warning dialog is displayed during the process, chances are the computer has been compromised and the Xcode version is poisoned.
Test is not foolproof, though
However, the expert warns that this simple verification is not foolproof in determining the breach since at the moment no samples of the malicious version are available.
The leaked document informs of the government agency’s efforts to create a rogue variant of Xcode in a presentation called “Strawhorse: Attacking the MacOS and iOS Software Development Kit.”
The functionality of the tool is also described, but there is no clear indication that the agency actually managed to deploy the operation; but given the capabilities of US intelligence organizations, this could have been achieved through a man-on-the-side attack, if everything functioned as expected.
 14 DAY TRIAL //
14 DAY TRIAL //