A spam campaign targeting businesses in the automobile industry in European countries has been observed to deliver Carbon Grabber, a piece of malware that uses the man-in-the-browser technique to collect data from web browsers.
The most affected country is Germany, accounting for 38% of the infections, followed by Netherlands with 31%, and Italy with 24%.
According to security researchers, Carbon also injects code in Microsoft Outlook, offering the attacker the possibility to read and send email message on behalf of the affected company.
Lionel Payet, threat intelligence officer at Symantec, says that the threat is delivered via an email message from fictitious company Technik Automobile GMBH.
Aimed mainly at customer service departments of the targeted companies, the message informs the recipient of an offer to purchase used cars, attaching a list with vehicles needed urgently.
The attachment is a malicious file, and once launched, it installs the Carbon Grabber malware on the system.
The researcher says that after decrypting another executable from its body, code is injected in Microsoft Outlook and in the processes of the most popular web browsers on the market: Internet Explorer, Mozilla Fiefox and Google Chrome.
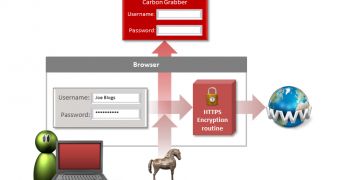
“The malware hooks the browser APIs, allowing it to steal information before it is encrypted and sent out to the network. Stolen information may include the user name and password for Outlook and information entered by the user when using a website to log into services such as online banking or internal Web applications for example,” writes Payet in a company blog post.
All the data intercepted through this technique, known as man-in-the-browser (MitB), is then delivered to a command and control (C&C) server.
Not just entities in the automobile business are targeted by the attackers, as Symantec has also registered infections on machines used in the public services (13%), as well as in the financial sector and charity works (9% in both cases).
However, the security company noticed that most of the victims (48%) affected by Carbon Grabber, detected as Infostealer.Retgate by its products, are familiar with services such as car rental, commercial transport and the secondary market for commercial and agricultural vehicles.
Carbon Grabber has been promoted on underground forums at the beginning of the year, the price for new customers being of $150 / €114 for the binary and $800 / €606 for the builder. For previous customers a price cut is applied, having to pay $50 / €38 for the binary and $300 / €227 for the builder.
The piece of malware is even advertised on YouTube, in a 17-minute demo video showing its full capabilities.
At the moment, the purpose of the attackers is unknown, but it is suspected that they are after banking information, since most of the time customer service departments are also responsible for financial tasks, apart from administrative activities.
 14 DAY TRIAL //
14 DAY TRIAL //