Scammers have changed their phishing game once more and are now trying to lure unsuspecting users into providing login credentials for their bank accounts, by consenting to receive messages from the institution that would be considered unsolicited by a recent anti-spam law in the US.
The US anti-spam law mentioned in the phishing message is fake and it is clear that the crooks took the idea from the real Canadian legislation that was passed recently, which states that in order to deliver emails to customers, businesses have to obtain their explicit consent.
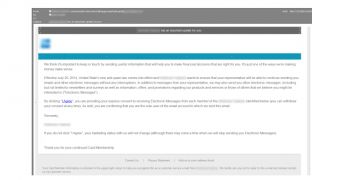
In the phishing email, the recipient is informed that the fake US anti-spam law is effective since July 20, and the bank requires permission to deliver electronic information to their inbox.
The text, provided by Symantec, seems legitimate, but the link for accepting the bank’s product information and messages should trigger alarm bells, since it is shortened with the Bit.ly service.
“By clicking ‘I Agree’ you are providing your express consent to receiving Electronic Messages from each member of the [BANK NAME] identified below (you can withdraw your consent at any time). As well, you are confirming that you are the sole user of the email account to which we sent this email,” is written in the message from the crooks.
Of course, following the link leads to a phishing page that requires logging into the online bank account. Everything entered into those fields is automatically sent to the cybercriminals, who will then be able to access the bank account, especially where no other forms of authentication, such as one-time password (OTP), are implemented.
While the text is carefully written and could fool some of the recipients into believing it to be legitimate, there are, however, some clues that reveal the email for the deceit that it is.
First of all, the shortened link. Financial institutions do not use URL shortening services in official communication.
Next is the URL of the phishing page, which, according to Symantec, does not suggest in any way that the page is hosted on the bank’s systems.
A more observant user would also notice that the accessed website does not use encryption for the communication between the client and the server (no “https://” and green padlock available in the address bar).
Another indication of the deceit is the news about the anti-spam law in the US. In case of this sort of legislation media sources would have undoubtedly informed the public.
 14 DAY TRIAL //
14 DAY TRIAL //