Ransomware with file encryption capabilities represents a problem that does not seem to come with a solution for the time being, as the amount of new samples for this malware family has increased dramatically, with CTB-Locker and CryptoWall being the most prominent exponents.
In a report released on Tuesday, researchers at McAfee Labs presented a dire situation regarding the crypto-malware threat in the first quarter of 2015.
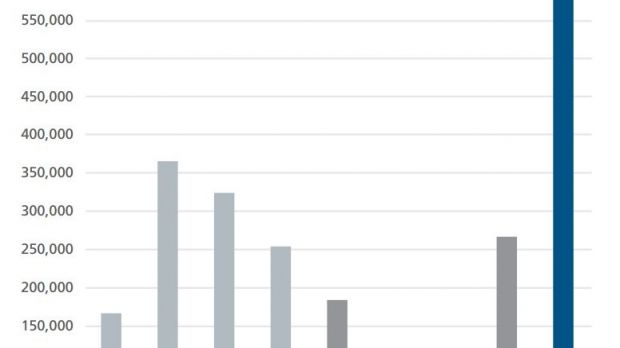
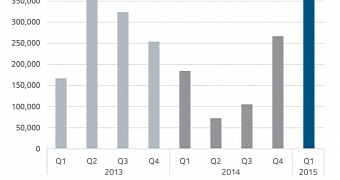
Telemetry data from the company showed a total of more than 720,000 new samples emerging in the first months of 2015.
This accounts for almost a threefold increase, considering that in Q4 2014 the company identified slightly over 250,000 new ransomware samples.
CTB-Locker uses affiliation program
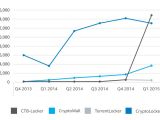
At the top of the list is CTB-Locker (Curve-Tor-Bitcoin-Locker), which started its ascension in December 2014 and shot to about 15,000 new variants at the beginning of 2015.
As the name suggests, the malware piece relies on strong encryption (elliptic curve cryptography) to lock the files up, uses command and control (C&C) servers in TOR anonymity network, and the ransom is demanded in bitcoins to lose the trace of the money.
According to Christiaan Beek from McAfee, CTB-Locker’s success is owed to clever techniques for evading detection. The researcher notes that “the presence of an affiliate program has allowed CTB-Locker to very quickly flood the market with phishing campaigns before systems have been updated with security software that can detect and contain the attacks.”
The ransomware is distributed via botnets operated by different cybercriminals, who receive in exchange a piece of the ransom paid by the victims (mostly from North America and Europe).
Depending on how many pay and the distribution costs (traffic redirects, exploit kits), profits can be between $8,000 / €7,100 and $10,000 / €8,900, the researcher says.
CryptoWall comes second, but is not less of a threat
With approximately 13,000 fresh samples in Q1 2015, CryptoWall falls in the second place as the most prevalent piece of ransomware for the period. It is now at version 3.0, which is distributed through Dyre botnet, Beek says in the report.
The infection chain also includes the Upatre malware downloader, which usually reaches the victim’s computer via spam. The first thing it does after installation is to funnel in Dyre.
Payment of the ransom fee is done only through a server located in Tor, which makes the operation more difficult to disrupt.
Another relevant threat for the analyzed period is TeslaCrypt, which became known for targeting a large number of file types used by popular games.
A recent report from FireEye revealed that the operators behind it made about $75,500 / €66,500 between February and April.
 14 DAY TRIAL //
14 DAY TRIAL //