The cybercriminal campaign in which the systems of the Council on Foreign Relations (CFR), the Capstone Turbine Corporation, and various other organizations have been targeted is far from being over.
Experts from security firm Avast, in collaboration with independent researcher Eric Romang, have identified several additional targets of the watering hole campaign, including the site of a major Hong Kong political party.
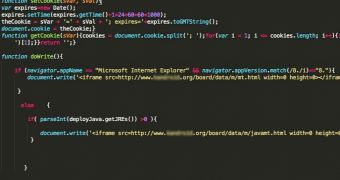
The party’s website is using not only the original Internet Explorer exploit – which Microsoft addressed on January 14 –, but also the latest Java vulnerability.
The cybercriminals are using a compromised site from South Korea to host the exploit files.
Interestingly, the new code is not targeting only browsers with certain supported languages. The Remote Administration Tool (RAT) that’s pushed onto the victims’ computers has been found to communicate with a domain hosted in Hong Kong by New World Telecom.
A detailed analysis of these latest attacks can be found on Avast’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //