A currently unfixed vulnerability in the iOS email client can be exploited by an attacker to send messages that can trick recipients into giving their Apple credentials or accessing malicious web pages.
The vulnerability was reported to Apple on January 15, but Jan Soucek, the researcher who discovered it, says that it was not addressed in any of the iOS updates released after version 8.1.2.
Proof-of-concept exploit code published
iOS is currently at stable version 8.3, with 8.4 being in beta stage of development and available only to registered developers.
Since five months have passed without Apple taking any action to solve the issue, the researcher decided to make public his findings and the proof-of-concept (PoC) code, in the hope that this would accelerate patching.
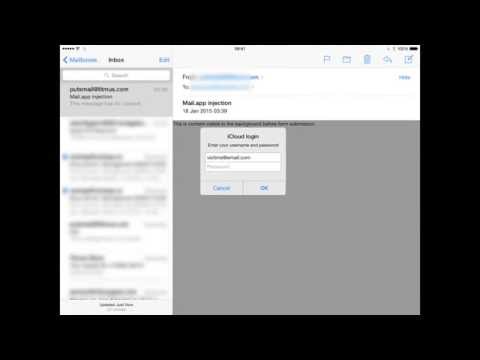
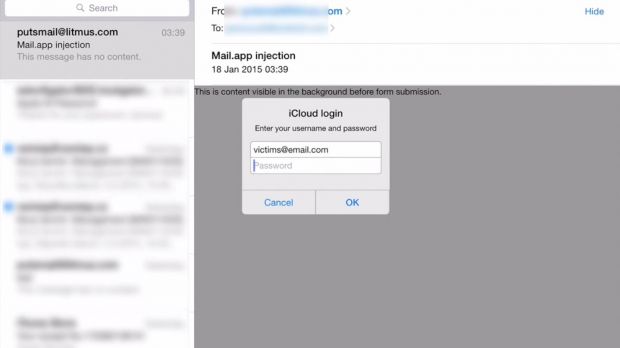
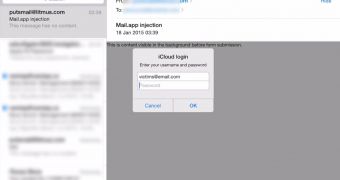
Soucek found that the HTML tag is not ignored by the Mail app, which can be exploited to replace the original content in an email with HTML from a remote location under the control of the attacker.
He also published a video (embedded below) to demonstrate the success of the PoC exploit, showing how the Apple login page pops up after receiving a malicious email.
To make the login dialog credible, Soucek relied on CSS code from Framework7, an open source HTML framework for developing mobile and web apps with the look and feel of native iOS.
Attack can be executed without raising suspicions to the victim
Although an email spoofing the login page can be sent without showing content from a different location, using the “http-equiv” attribute provides flexibility and permits the fake login page to be loaded in the correct context.
“When you use this http-equiv method, the remote page containing login form gets loaded only on vulnerable iOS device. It wouldn't make much sense if it asked for Apple ID credentials with iOS-styled dialog box when opened in Outlook or Gmail on the desktop, right? Because the redirect meta tag gets ignored by other mail clients, it will look like a regular e-mail message,” Soucek explains.
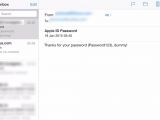
His code can also determine if the recipient visited the page in the past by checking the cookies, thus preventing the spoofed page to be displayed each time the malicious email is opened.
Furthermore, since the sign-in page is not actually delivered to the recipient, it can be replaced on the web server with the original email message, or with other sort of malicious content.
Soucek says that the “vulnerability can be used for anything that requires HTML tags not supported by Mail.app.”
One way to protect against such an attack is to enable two-factor authentication for Apple ID.
Demo of an attack via iOS Mail app:
 14 DAY TRIAL //
14 DAY TRIAL //