A security flaw in Facebook’s comments module allowed a remote unauthenticated attacker to delete or add messages to a timeline without any user interaction.
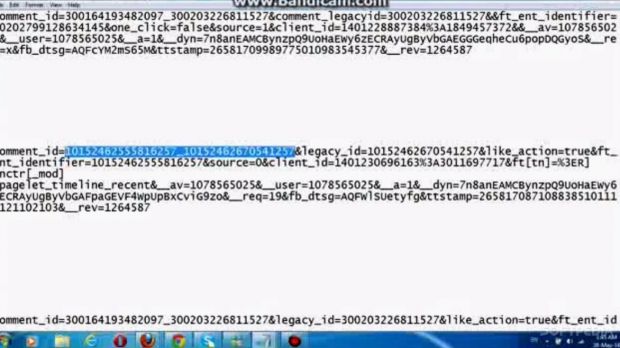
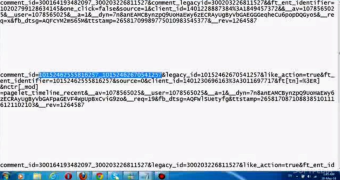
An independent security researcher by the name Joe Ballhis discovered that he could capture the session traffic for a request to delete a comment in an authenticated account, thus learning the comment ID and legacy ID values.
The two codes would also be available in the case of a “like” request for the timeline content of a different user.
Severity score of the flaw disputed
Ballhis found that by replacing the two IDs from the “like” request with the ones obtained from the “delete” request, and replaying it with the modified version, an attacker could remove a message posted on any user’s feed.
“Remote attackers with low privileged user accounts are able to delete postings of other users without auth,” an advisory on the matter says.
The estimated severity rating for the glitch is 9.1, based on the calculator at the Common Vulnerability Scoring System. However, this is not an official estimation of the impact and other researchers contest the 9.1 criticality.
Scott Arciszewski, who reported a lack of CSPRNG in WordPress, expressed his doubt about the rating, while Julius Kivimaki went further and made some calculations himself; the result was an overall score of 7.2 and a base one of 6.8.
"Even though deleting everything is kind of a big deal, it still does not get you anywhere near that CVSS score," Kivimaki says, pointing to his result.
Disclosure was allowed in Q1 2015
The researcher reported the vulnerability to Facebook in 2014 and the developers issued a patch for the platform. He was also awarded $12,500 / €11,000 for his finding and was included on the list of whitehats who reported security flaws to the company in a responsible manner in 2014.
Although a fix had been implemented last year, Ballhis was requested by the social network company to refrain from making the problem public until the first quarter of 2015.
Recently, Facebook repaired another vulnerability, one that allowed an individual to delete the album images of any user on the social network.
The developer who discovered the glitch received the same reward as Ballhis and said that the fix came only two hours after Facebook confirmed the problem.
Ballhis made a video that exposes the steps taken to exploit the security bug:
 14 DAY TRIAL //
14 DAY TRIAL //