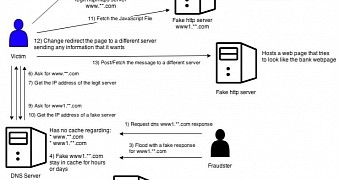
Cybercriminals in Brazil have resorted to a new method to steal the much coveted boletos, a nation-wide payment method, by poisoning the domain name system (DNS) entry used by a bank’s website so that the IP address to the legitimate location point to a site controlled by the cybercriminals.
Boleto payments are highly popular in Brazil. They consist in a voucher generated by banks that can be used instead of payment cards. An expiration date is set for each of them, defining a time frame during which merchants can accept it.
When they expire, the customer can re-generate another one, with a different identification number, through online banking services.
When a website is accessed, its name is converted into its IP address by a DNS server maintained by the ISP (Internet Service Provider). If the DNS server is compromised, attackers can assign any website an address under their control, in order to point visitors to malicious content.
This method has been observed recently by security researchers at RSA to be employed by Brazilian cybercriminals to carry out Boleto fraud, by altering the DNS entry for a temporary period of time.
Crooks poison DNS cache to point to fraudulent content
In the attack discovered by RSA, the crooks changed the IP used by the bank to load a JavaScript resource. Thus, when the customer requests the resource, they are served a malicious variant, without suspicions being raised.
Applied to the boleto fraud, a customer is served a fraudulent voucher upon applying for receiving a new one with a valid expiration date, while the details for the legitimate voucher are sent to the fraudster’s account.
The DNS cache poisoning attack begins with the threat actor making a DNS request for the target domain to a local DNS server that caches the addresses for a period of time.
If there is no record for the requested website, the server has to contact a root server; but before an answer is received, the attacker starts flooding the local DNS server with fake responses for the specified website. In the end, the response from the root is ignored and the information sent by the attacker is recorded.
 14 DAY TRIAL //
14 DAY TRIAL //