A security problem discovered in the Box Sync allows an unauthorized individual, if they know where to look, access to highly sensitive data used by companies to connect to the cloud, API keys and secrets for both Mac and Windows platforms.
If the application is used in an enterprise environment, chances are that its configuration files are available on different websites for collaboration between developers of the same company.
Finding the coveted configuration file is not easy
GitHub is one of the most popular collaboration platforms for developers and multiple tools have been created to scan its content in search of sensitive data left unprotected by their owners.
Pepijn Bruienne, a Mac administrator trying to find an easier way to deploy Box Sync to multiple clients, dug deep into the folder structure of the application in search of a configuration file that would help with making the update task less time-consuming.
After going through multiple folders, some documenting about the contents of a certain file type (Python PYO), and decompiling Python code, the admin found a reference to a location with a file containing configuration options (/Library/Preferences/com.box.sync.plist).
“Eureka!,” wrote Bruienne in a blog post on Saturday. “This file is normally not to be found on systems with Box Sync installed and configured for the user, so this is a great start. Some more searching reveals the _overridable_settings list in configuration.py which contains a key named auto_update.enabled,” he added.
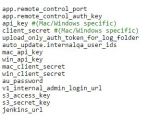
Cache of highly sensitive data discovered
Even if the mission was basically accomplished, the admin continued to look around in the “base.py” and “auto_update_release.pyo,” checking their contents. What he found was serious reason for concern, as in the hands of an attacker it could spell disaster for the company.
Among the configuration files encountered there were Amazon S3 access and secret keys, which are in fact the username and password for logging into the data storage service provided by Amazon. These allow permission for uploading, downloading or controlling user permissions.
However, this is not all being exposed, as API keys, internal user IDs, URLs and passwords are also available.
All this could allow an attacker complete access to the data stored in the cloud by a company as well as the possibility to tamper it, for compromising the network.
The developer says that Box was informed about the findings in early January and the cloud storage service issued on February 6 a new version of the application, 4.0.6035, which eliminates the security risks. The fresh revision is currently available for download for Windows and Mac.
Any admin deploying Box Sync at enterprise level, as well as regular users, are strongly advised to update the product to its latest release.
“There is no way of knowing who else has been aware of the exposed information before me and whether or not it may have been used to access Box customer data. This is especially important in environments that use a managed software update workflow which may be holding back automatic updates until specific action is taken by an admin,” the blog post from Bruienne adds.

 14 DAY TRIAL //
14 DAY TRIAL //