Yesterday, shortly after the world had learned of the Boston Marathon Bombings, we released an alert, advising users to be on the lookout for malicious schemes that might leverage the incident. As expected, cybercriminals have already stepped into play.
Experts from security firm Kaspersky have identified spam emails entitled something like “2 Explosions at Boston Marathon “or “Explosion at Boston Marathon.”
The messages contain links that appear to point to a file called “news.html.”
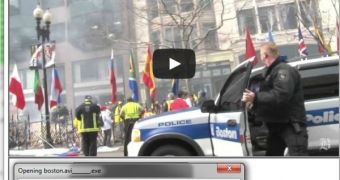
Users who fall for it and click on the links are taken to a page that displays YouTube videos covering the bombings. While there’s nothing malicious about the clips themselves, after a 60-second delay, the website prompts victims to download an executable file called “boston.avi____exe.”
Once it infects a computer, this piece of malware, Trojan-PSW.Win32.Tepfer, attempts to connect to several IP addresses in Taiwan, Argentina and Ukraine.
The SANS Technology Institute’s Internet Storm Center (ISC) has also issued an advisory to warn users about fake domains registered shortly after the attack in Boston.
The ISC’s John Bambenek reports that at least 234 potentially fake domains have been registered.
“Some of these are just parked domains, some are squatters who are keeping the domains from bad people. A couple are soliciting donations (one is soliciting bitcoins, oddly enough),” Bambenek explained.
Fake Twitter accounts have also emerged, some asking for donations, while others are simply exploiting the Boston Marathon bombings to gather followers.
Here are some basic rules you must follow in order to avoid falling victim to Boston Marathon scams:
- don’t click on links or attachments that arrive in unsolicited emails; - beware of new websites related to the event, especially charities and news sites; - don’t donate money to charities you don’t trust; - thoroughly check out an organization before giving it any money; - avoid forwarding/sharing/retweeting suspicious emails/posts, especially if they contain links.
 14 DAY TRIAL //
14 DAY TRIAL //