Cybercriminals are distributing a variant of the notorious ZeuS Trojan by hiding it inside innocent-looking screensaver (.scr) files attached to bogus order inquiry emails.
“My name is Tc Koung and I am the purchasing officer for Aracom Business Group with head office based in the U.S.A. We got your contact and recommendation from one of your old customers and we would like to place a large order for your products for our next trading year,” read the fake emails spotted by MX Lab experts.
“Please, find attached our order list, 3D pictures and drawings for your review. Kindly quote your best prices for each product in the list. You are to quote FOB and payment terms as well,” the notifications continue.
Researchers say that these emails have a scan of a legitimate-looking document attached to them. However, the messages also contain a couple of URLs to “view slideshow” and “download all as a zip.”
The document contains a link that, similarly to the other two URLs, points victims to the website of a hotel from Vientiane, the capital city of Laos.
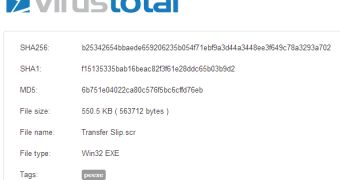
The cybercriminals have compromised this website and planted the malicious .scr file on it. Once it’s executed, the .scr file – detected as Trojan/Win32.Zbot or Win32:Rootkit-gen – creates a process called votuiqo.exe, and several registry entries.
When experts analyzed it, the Trojan’s signature was detected by only 28 of the 46 antiviruses from VirusTotal.
Scam emails that purport to come from Aracom Business Group have been around for quite some time.
These particular types of scams can be highly effective in targeting companies. It’s likely that the cybercriminals are trying to plant the information-stealing Trojan inside organizations’ networks in an effort to raid their bank accounts.
If you come across such emails, delete them. If you’re already a victim, scan your computer(s) with an updated antivirus and keep a close eye on your bank account.
 14 DAY TRIAL //
14 DAY TRIAL //