Security researchers found that a new variant of the malware family BlackEnergy has been uploaded to VirusTotal, first from Ukraine, and a few minutes later, someone from Belgium checked the file.
F-Secure notes in a blog post that on Friday someone submitted to Google’s VirusTotal a ZIP archive containing an executable file having Microsoft Word’s DOC extension.
Upon checking the scanning service for traces of the respective DOC, they found that it was submitted from Belgium. The difference between the two submissions is exactly five minutes, so there is room to speculate that the two actions are somehow related.
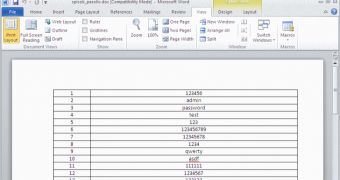
The ZIP archive and its content have the same name, the difference consisting in spelling (one uses the Cyrillic alphabet, the other the Latin one), which means “password list.”
Having a document extension instead of an executable one could be a mistake of the author, who could have forgotten to make it a double extension so that the threat could be deployed.
It seems that the fresh variant gave up some of the components used in the previously detected one and “no longer uses a kernel mode component for injecting the user mode DLL into svchost.exe;” the reason for this might be to avoid raising suspicions because of the driver signing protection present in the recent Windows operating systems.
However, it relies on a user-mode dropper in order to load the malicious DLL with the use of rundll32.exe. As a result of the analysis, researchers say that “the user mode DLL has also been rewritten to support the change.” According to them, the timestamp on the code is June 26, 2014.
Further investigation revealed that the dropper would open a decoy Word file in order to mask malicious activity. The file contains a set of weak passwords, so it is connected with the “password list.”
One scenario would be that the criminals use spear-phishing to reach the victim, and that the message might warn of the risks of using weak passcodes or that the strings presented in the document should not be used.
F-Secure researchers who analyzed a previous sample spotted on VirusTotal noticed that it had been created to work on modern versions of Windows (8 and 8.1). However, since it was not signed, the driver verification mechanism in the operating system would prevent infection of the machine.
Since the latest sample has been stripped of the kernel mode component, it is clear that criminals are making efforts to adapt it to the new environments in order to reach their goals.
 14 DAY TRIAL //
14 DAY TRIAL //