An unknown entity has been discovered to use a fake Border Gateway Protocol (BGP) broadcast to absorb traffic from 51 crypto-curency mining pools at 19 hosting companies, which includes Amazon, Digital Ocean, OVH, and other large hosting services.
Researchers at Dell SecureWorks’ Counter Threat Unit (CTU) found that cybercriminals conducted this activity between February and May, 2014, raking in profit estimated around $83,000 / €62,000.
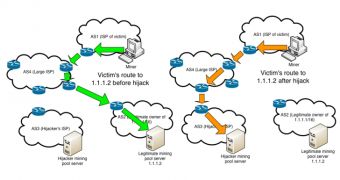
The suspicious activity was first flagged on a forum dedicated to crypto-currency discussions, where several users reported that their mining systems redirected to an unknown IP address and used the Stratum protocol.
Stratum, a JSON-based TCP connection, is employed for miners to communicate with the pool server. The JSON enables monitoring the communication.
Pat Litke and Joe Stewart from CTU write in a blog post that immediately after the connection to the attacker’s IP address was established, the “miners continued to receive work but no longer received block rewards for their mining efforts. Hijackers harnessed miners' hashing power by redirecting legitimate mining traffic destined for well-known pools to a malicious server masquerading as the legitimate pool.”
According to the researchers, Bitcoins were not the only target of the hijacker as Dogecoins were stolen, too; the amount was 8,000 Dogecoins, though, which amount to a little over one US dollar.
The identity of the hijacker remains unknown at the moment, but the two researchers say it could be a current or former rogue employee of the ISP, or a hacker.
 14 DAY TRIAL //
14 DAY TRIAL //