Communication with the command and control (C&C) server via Tor used by a version of Bifrose backdoor could be leveraged by IT administrators to detect the cyber intrusion.
Tor (The Onion Router) is a network of computers designed to anonymize communication between two parties by concealing their location. It is generally used to fight censorship and to protect the privacy of the users.
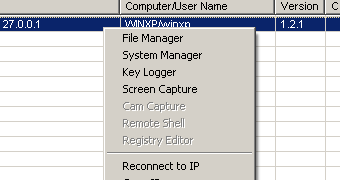
While investigating an attack against an undisclosed device manufacturer, security researchers at Trend Micro discovered a build of Bifrose malware that uses this network to receive instructions from its operator.
Bifrose, also known as Bifrost, is mostly famous for its keylogging capabilities, but the build encountered by the researchers integrates other functions, such as uploading and downloading data, create and delete folders, executing command lines, renaming files, as well as manipulating application windows through keyboard and mouse events.
Because it communicates with its handler through TOR anonymity network, the experts say that it is possible for system administrators to learn of an attack relying on this Bifrose variant by detecting Tor activity in the network.
Another clue of its presence is the existence of the “klog.dat,” which is associated with Bifrose’s keylogging activity.
Generally, operations on the network, like logins and email sending, at unusual times may also indicate malicious activity. These are also to be taken into consideration in the case of Bifrose.
 14 DAY TRIAL //
14 DAY TRIAL //