A new piece of financial malware spotted by security researchers targets only users in Japan by creating a malicious proxy service on the victim’s computer and filtering out any IP addresses outside the area of interest.
Although the malware relies on basic proxy-changing tactics to direct the victims to rogue pages impersonating Japanese banks, it uses sophisticated social engineering to achieve its goal.
Malware tip-toes through the installation process
Security researchers at IBM Trusteer analyzed the malware piece and named it after Tsukuba Science City in Japan.
They noticed that the distribution method for the banking Trojan is email spam, and after infecting the computer, it runs a set of routines designed to hide the malicious activity that consists in stealing credentials and personally identifiable information by making the victim believe that they’re browsing a legitimate website.
IBM threat engineer Dani Abramov says in a blog post on Wednesday that Tsukuba’s actions are calculated and selective from start to end.
It masks its installation, includes anti-analysis tactics, and acts only if research environments and proxy detection tools are not present on the infected machine. Furthermore, it determines from the start if the victim fits its list of targets.
After installing fake root certificate, which is added with the name of a legitimate one - “typically, that name is ‘VeriSign Class 3 Public Primary Certification Authority - G5,’” Abramov says - it proceeds to making the proxy modifications, which are applied to Internet Explorer, Google Chrome and Mozilla Firefox.
Crooks direct victims to interactive fake pages
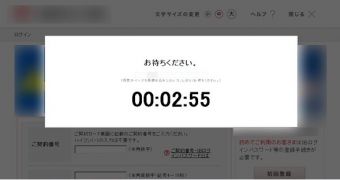
In the final stage of the attack, Tsukuba uses interactive web-fakes to capture the sensitive information from the victim.
This is similar to phishing but the content is continuously pulled from the legitimate website of the bank and dynamic interaction is available, with pop-ups being displayed to ask for the details the cybercriminals need to take over the financial account.
Security researchers also observed requests for uploading scans of official documents such as passports. “Looking at similar malware of Tsukuba’s grade, this extensive social engineering component definitely goes far beyond the common,” says Abramov.
The fake screens are designed to rush the victim into action as counters to complete the required tasks are displayed on the fake pages. Instructions to input easy-to-read information are also provided.
These requests may ring the alarm bells for most users in other parts of the world, but Japan has been protected by a language barrier until recently, as cybercriminals are mostly targeting English-speaking people.
 14 DAY TRIAL //
14 DAY TRIAL //