Malvertising attacks are becoming more and more common and it appears that not even YouTube users are safe. Security researchers from Bromium have come across a YouTube link that led users to an exploit kit website.
According to experts, cybercriminals compromised an ad network that’s used to serve advertisements on YouTube. The ad network in question hosted the Styx exploit kit.
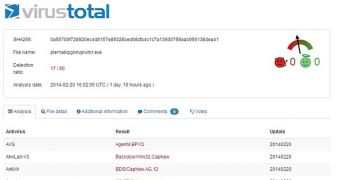
This particular exploit kit is designed to leverage Java vulnerabilities in order to push malware onto infected devices. In this case, the malware that’s being distributed is Caphaw, a threat that’s designed to harvest banking information from victims.
The command and control server used by the cybercriminals appears to be hosted in Europe and it relies on a domain generation algorithm (DGA).
Bromium has notified Google of the attack, but so far, there are no details on how the cybercriminals have pulled this off.
Update. Google says a rogue advertiser is behind the campaign. The operation has been shut down, and Google is making some changes to prevent such attacks in the future.
Here are the steps of the attack as described by Bromium: 1: User watches a YouTube video; 2: He/she sees a thumbnail of another video (*.JPG); 3: User clicks on the thumbnail and watches the video. In the background the user gets redirected to a malicious ad served by Googleads (*.doubleclick.net); 4: Malware redirects the user to ‘foulpapers.com’; 5: Foulpapers.com iframes the aecua.nl; 6: aecua.nl delivers the exploit (Styx exploit kit).
 14 DAY TRIAL //
14 DAY TRIAL //