F-Secure researchers have identified a malicious element that is able to infect the computers of Mac OS, Linux and Windows users.
The curious attack starts on the compromised website of a Colombian transport organization. When the user visits it, he/she is presented with a window that requests permissions to run a Java applet that’s most likely generated with the use of the Social-Engineer Toolkit.
Once it’s executed, the .jar file determines the type of the operating system running on the target machine.
Based on the detected platform, the victim is served one of three pieces of malware: Backdoor:OSX/GetShell.A, Backdoor:Linux/GetShell.A or Backdoor:W32/GetShell.A.
They all establish connection to 186.87.69.249, from where they receive additional commands.
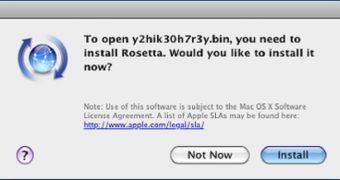
However, since the backdoor designed for Mac OS X is a PowerPC binary, in case the platform is Intel-based, the user is requested to install Rosetta.
 14 DAY TRIAL //
14 DAY TRIAL //