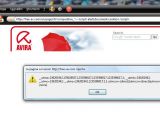
A hacker has disclosed several XSS flaws on free-av.com, online home to the free version of Avira AntiVir. The vulnerabilities that could have been used for redirection or hijacking session cookies have been patched by the antivirus vendor.
The bugs in the Avira-controlled website have been discovered by a hacker going by the handle "Methodman," who is affiliated with a group known as ']['€AM€LiT€ (Team Elite). According to its own description, Team Elite is a group of programmers and security enthusiasts who develop various freeware tools including web server and chat software.
In keeping with the screenshots and the proof-of-concept code released by Methodman, by manipulating the URL of several pages on the free-av.com website an attacker could have forced redirection to a third-party link, launched alerts or disclosed session cookies. Such vulnerabilities are dangerous, because they can be exploited in order to instrument phishing campaigns and other attacks with the help of social engineering techniques. In this particular case they posed even a greater risk, since they affected a website controlled by a popular antivirus vendor, which users tended to trust.
Fortunately, the company was prompt to react when informed of the problem. In a reply to our notification e-mail, an Avira representative confirmed that the programmer responsible with the maintenance of the affected website was able to reproduce the attack and addressed the issues by enforcing a stronger URL validation. Furthermore, he maintained that the company had not been informed by the hacker prior to the disclosure, nor had it ever received other notifications of similar problems.
He also pointed out that, as a precaution against all web vulnerabilities (SQL injection, XSS etc.), the company was undergoing an internal audit of its web-related applications. "A team of programmers is verifying and standardizing the way in which the validation of all parameters received from Web applications is performed," the spokesperson wrote.
Methodman has recently disclosed similar XSS vulnerabilities affecting the website of Kaspersky Labs. The hacker is likely to have been inspired to target AV vendors by the similar acts of another self-confessed ethical hacking group called HackersBlog, which has recently disclosed various SQL injection vulnerabilities in the websites of Kaspersky, Bitdefender, F-Secure and Symantec.

 14 DAY TRIAL //
14 DAY TRIAL //