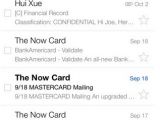
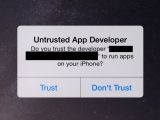
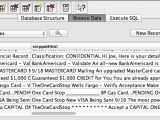
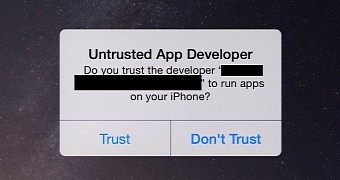
Because iOS does not enforce matching certificates for apps with the same bundle identifier, rogue apps can be installed on iDevices, a security firm discovered recently.
Apple has issued a response denying the existence of any such occurrences in the wild, while advising users to only download and install software from trusted sources.
The Masque Attack
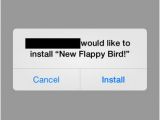
Revealed earlier this week, a vulnerability in Apple’s mobile operating system allows for an arbitrary title to be displayed "that lures the user to install it, but the app can replace another genuine app after installation,” reported FireEye earlier this week.
“All apps can be replaced except iOS preinstalled apps, such as Mobile Safari. This vulnerability exists because iOS doesn't enforce matching certificates for apps with the same bundle identifier. An attacker can leverage this vulnerability both through wireless networks and USB,” FireEye added.
Rogue apps installed using this technique are able to mimic the original app’s GUI and trick the user into punching in their user name and password. Such apps can access sensitive data from local data caches, perform background monitoring, and gain root privileges. The user is unaware he / she is using a fake app because it looks and works the same, while the device itself doesn’t behave any differently.
Apple issues a typical response
Not surprisingly, the company doesn’t agree that the Masque attack is reason for panic, and in fact, points out that there are no reported cases in the wild.
In a statement provided to iMore, the Cupertino tech giant says, “We designed OS X and iOS with built-in security safeguards to help protect customers and warn them before installing potentially malicious software.”
“We're not aware of any customers that have actually been affected by this attack,” the company added. “We encourage customers to only download from trusted sources like the App Store and to pay attention to any warnings as they download apps. Enterprise users installing custom apps should install apps from their company's secure website.”
Going by Apple’s response, one could assume that iOS actually doesn’t suffer from a vulnerability. Rather, it has particularities that can be exploited, but that don’t necessarily require patching because it would fundamentally change the way the system works.
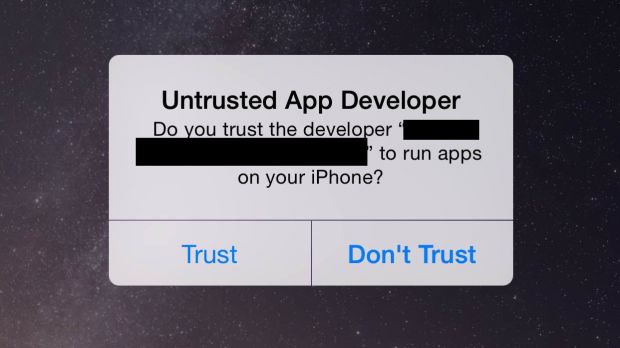
An obvious solution to the problem is to pay attention to the Untrusted App Developer alert. Another way you can make sure you don’t end up installing malware is to only download apps from the iTunes App Store.
 14 DAY TRIAL //
14 DAY TRIAL //