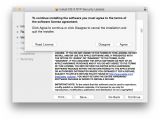
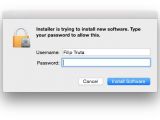
Apple this week rolled out its first-ever automated security patch for OS X customers, requiring users to download a small package and follow the steps outlined by the installation wizard without as much as a single reboot.
Revealed by the Department of Homeland Security and the Carnegie Mellon University Software Engineering Institute via traditional security bulletins, the bugs affected the network time protocol (NTP) component that handles time-related matters and is crucial for syncing clocks.
Apple was only one of the software vendors whose systems had been affected by the flaw. The vulnerability is a critical one, hence the company’s decision to speed up the patching starting now.
Available for Yosemite, Mavericks, and Mountain Lion
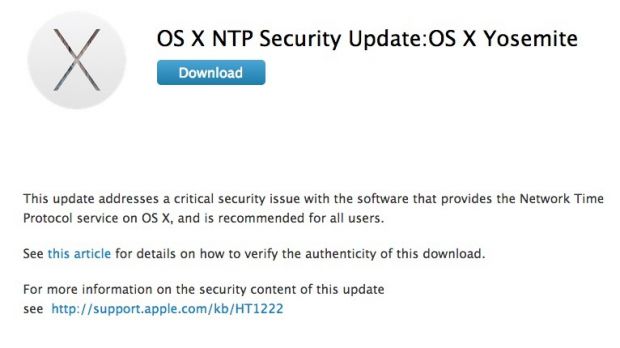
According to the documentation put forth by the Cupertino company, OS X NTP Security Update “addresses a critical security issue with the software that provides the Network Time Protocol service on OS X, and is recommended for all users.”
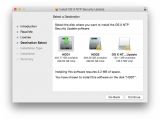
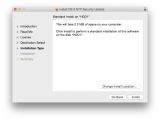
The update has been optimized to patch the flaw on three separate Mac OS versions – Yosemite, Mavericks, and Mountain Lion – and is offered as three different installers, each designed to work on a single OS version, while refusing to run on others.
Apple directs interested parties to the legendary HT1222 support article that details the newest security-centric efforts in Cupertino, California. There, customers will find bulletin HT6601 titled “About OS X NTP Security Update,” which discusses the patched flaw at length.
Available for OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, and OS X Yosemite v10.10.1, the vulnerability leveraged several issues in ntpd that would have allowed an attacker to trigger buffer overflows and ultimately “execute arbitrary code.” Crediting Stephen Roettger of the Google Security Team for originally uncovering and reporting the bug, Apple says the issues are addressed by the NTP update through improved error checking.
How to make sure you’re patched
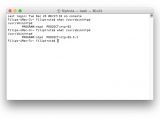
Apple says you can check your current ntpd version using the Terminal. Users must type in the following command:
what /usr/sbin/ntpd
After applying the patch (i.e. downloading and installing the OS X NTP Security Update), users will again need to verify their ntpd version using the Terminal, just to make sure. Mountain Lion users should see ntp-77.1.1, Mavericks customers should be shown ntp-88.1.1, and Yosemite needs to be ntp-92.5.1, post update.
If these numbers show up on your screen as well, you’re patched. Unlike with previous security updates from Apple, this one will not force the computer into a reboot.
Download OS X NTP Security Update for any of the three OS versions using the supplied link and patch your system today.
 14 DAY TRIAL //
14 DAY TRIAL //