About six percent of all the Android apps are built on a vulnerable version of Apache Cordova platform that allows a potential attacker to steal sensitive information, such as login credentials.
Security researchers warn that numerous banking apps rely on Apache Cordova and, as such, the financial information of the users is at great risk since cybercriminals could steal the banking credentials and tip the financial balance in their favor.
The flaw, cross-application scripting (CAS) via Android Intents (CVE-2014-3500), was uncovered by the IBM Security X-Force Research team, who contacted the Cordova team about their findings, allowing them to come up with the necessary patches.
“Intents” is what facilitates inter-app communication on Android when an app is executed in a sandboxed environment in order to preserve confidentiality and integrity of the information.
Apart from this, the IBM security team revealed two more vulnerabilities, one allowing to bypass the Cordova whitelist for non-HTTP URLs (CVE-2014-3501) and another that presented the risk of leaking data to other apps via URL loading (CVE-2014-3502).
By leveraging them, an attacker can access the sensitive information and exfiltrate it from the victim’s mobile device.
The result is a new Apache Cordova version for Android. All releases prior to 3.5.1 are affected by the bug, which permits execution of malicious JavaScript code in the context of Cordova-vulnerable apps.
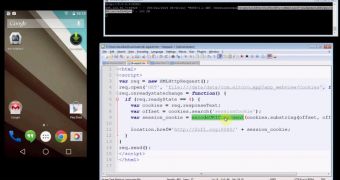
“The IBM team’s analysis shows it is extremely easy for an attacker to exploit this vulnerability. Under certain circumstances, it can also be remotely exploited to steal sensitive information, such as cookies associated with the Cordova-based application, by naïve mobile browsing to a malicious website (better known as a drive-by exploitation),” reads a post from Roee Hay, leader of the application security research team at IBM.
He also provides an attack scenario, where the attack is conducted remotely, with the victim being lured to an online location containing malicious JavaScript that exploits the vulnerabilities in Cordova; this offers the bad actor the possibility to steal sensitive information in an application.
In the case of a banking application, the stolen credentials can lead to activities such as transferring money from the bank account.
According to Hay, opening the gate to incoming Intents messages means increasing the attack surface, because components of the application can be attacked locally by malware.
In a more severe case, these can also be attacked remotely if certain conditions are met, with a single click to a malicious website that delivers the exploit code.
Together with David Kaplan, Hay made a video with the exploit in action, proving a remote drive-by attack leveraging the vulnerabilities they discovered. You can check it below.
 14 DAY TRIAL //
14 DAY TRIAL // 