The traditional malware detection approach is far from being sufficient, especially in corporate environments, as antivirus products could take months before adding the routines for recognizing some of the more complex threats.
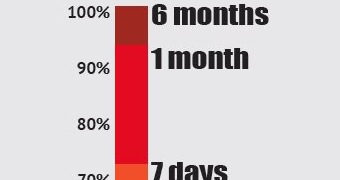
A study from Damballa, a security company offering solutions against advanced cyber threats, revealed that malware could spend as much as six months on a system before it is identified using signature-based detection.
AV products detected 93% of the malware after a month
During a nine-month period, the researchers analyzed a sample set of thousands of files delivered for review by enterprise customers and had it scanned by four of the most popular antivirus products currently on the market.
The company found that in the first hour from submission, only 30% of the malware database could be identified by the products as a threat. After a day, the detection rate increased to 66% and the improvement continued after a week, when 72% of the malicious database entries were labeled as a threat.
Damballa researchers systematically re-scanned the files in order to see the amount of time needed by the maintainers of the antivirus products to add the correct signatures.
A month into the experiment, 93% of the samples were detected as malicious. The more time a threat spends on a system, the higher the chances are that attackers managed to reach sensitive areas or to exfiltrate sensitive information. According to Damballa, the 100% detection rate was achieved after more than six months.
Multiple detection mechanisms are available
Although this finding is worrying, it is worth noting that an antivirus product includes multiple layers of defense and does not rely solely on signatures to catch malware, such as behavioral analysis, reputation, or network controls.
Moreover, companies have more security controls at their disposal to catch suspicious activity, intrusion detection/prevention systems playing a very important role.
All these should help identify possible threats and lower the risk of compromise as they are checked by the security teams.
Damballa’s experiment was carried out on a small sample set, but in a real-world scenario companies receive about 17,000 malware alerts on a weekly basis. According to a study from Ponemon Institute, 705 of them actually receive the attention of the security team, who has to sift out the real threats from false positives.
With a high volume of alerts to analyze, the security team may not have sufficient time to go through all of them, which may lead to an increased malware dwell-time on the system.
“Dependence on prevention tools simply isn't enough in this new age of advanced malware infections; attackers can morph malware code on a whim, yet organizations have a finite number of staff to deal with the barrage of noise generated from security alerts. We urge taking a fresh “breach-readiness” approach, which reduces dependence on people and legacy prevention tools,” comments Brian Foster, Damballa's CTO.
 14 DAY TRIAL //
14 DAY TRIAL //