Fraudsters have been given free advice on how to increase the success of phishing campaigns leveraging emails purporting to be from Student Loans Company (SLC), as the organization failed to enforce proper security against domain spoofing.
Before Christmas, SLC foresaw a surge in phishing attacks that relied on its reputation to trick recipients into accessing malicious links and informed that all its official notifications would come from a specific email address, [email protected].
Domain is not protected against spoofing
However, the company did not take into account the fact that the domain slc.co.uk did not benefit from protective rules that prevented it from being spoofed. As such, the email address could be impersonated by fraudsters.
Given that students were already informed that communication from SLC would be delivered from that particular email address, cybercriminals could take advantage of the oversight and impersonate official messages, as the seed of trust into the contact detail had already been planted in the potential victims.
Paul Mutton of Netcraft, a UK-based firm that offers Internet security services, says that “slc.co.uk does not have a Sender Policy Framework record,” which would apply restrictions to authorized senders based on specific rules. In lack of such a policy, anyone could forge the email address in order to conduct illegal activities.
“If students infer from the SLC's advice that all emails from [email protected] will be legitimate, then fraudsters will be able to carry out much more convincing phishing attacks simply by spoofing emails from this address,” he wrote in a blog post on Thursday.
On top of this, it seems that a DMARC (Domain-based Message Authentication, Reporting and Conformance) record is also missing. Domain owners have this mechanism at their disposal for defining the authentication options for email addresses claiming to originate from their domain.
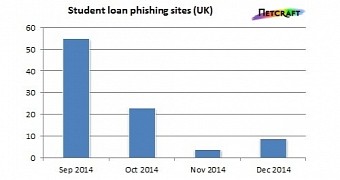
Low phishing activity recorded in December in UK
Luckily for SLC, it appears that phishing attacks were not that numerous during the Christmas holiday. “In fact, not a single student loan phishing site has been blocked by Netcraft since before Christmas day,” Mutton says.
This does not mean that the attacks are not still likely to occur, though. Until SLC fixes the issue and applies the necessary settings to thwart efforts of spoofing its email addresses, students in the UK are still at risk of falling for phishing attacks masked as SLC communications.
Cybercriminals are skilled at social engineering and can make fraudulent messages appear legitimate in order to serve malicious links or attachments.
 14 DAY TRIAL //
14 DAY TRIAL //