The recently launched Mega service has caused a lot of controversy. The site is not working properly, some security issues have been identified and, even Anonymous hackers have turned their back on it, calling Kim Dotcom a snitch.
One year ago, when US authorities took down Megaupload, the Anonymous movement was the first to protest. They showed their support for the file sharing service by launching distributed denial-of-service (DDOS) attacks against the FBI, the Department of Justice, the White House, and various anti-piracy sites.
Now, the tables have turned. Anonymous hackers say they’re boycotting Mega services because Kim Dotcom helped US authorities bring down other file-sharing websites.
“Why is Kim DotCom free while other file sharing pioneers still rot in jail? BECAUSE HE SNITCHED,” the hacktivists wrote, pointing to a Wired article that details the cooperation between Megaupload and US authorities.
“We seriously regret helping Kim DotCom with PR for MEGA. We were not aware he was a [expletive] snitch rat,” they added.
“In solidarity with NinjaVideo pirates rotting in jail after Kim DotCom snitched them out to DHS, we call for a boycott of all #MEGA services,” YourAnonNews wrote on Twitter. “Megaupload actively collaborated with the investigation. Pirate-on-pirate crime is unacceptable.”
“The difference between Sabu and Kim Dotcom's snitching?” the hacktivists wrote in a separate statement.
“Not only did Kim Dotcom have a choice to not engage in snitch behavior, instead of looking out for his customers and integrity of Megaupload and challenge the government's requests to retain the data by making a public spectacle out of the DHS's request, he went along with their requests to keep the warrants secret, legitimizing their culture of secrecy.”
As part of this boycott, some hackers have already taken credit for Mega’s downtime, claiming to have launched DDOS attacks against the website.
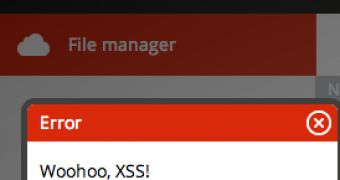
Anonymous is not Mega’s only problem. A number of security experts have started pointing out the existence of various issues: encryption keys stored online, and at least a couple of cross-site scripting (XSS) vulnerabilities.
In addition, a researcher claims to have developed a tool, dubbed MegaCracker, which is capable of cracking password hashes embedded into email confirmation links.
 14 DAY TRIAL //
14 DAY TRIAL //