The latest tactic adopted by the operators of the Angler browser-based attack tool makes it difficult for researchers to follow the redirection chain that leads to the malicious ad and the network serving it, causing the drive-by attack.
In a redirection chain, each new page accessed receives a request from the previous one containing the address in a field called HTTP referer. This allows tracking down the path followed by a user from one page to another.
Gap in the redirect chain reproduced on major browsers
Threat intelligence analyst Yonathan Klijnsma from security company Fox-IT found that the HTTP referer in the pages taking to the domain hosting the Angler exploit kit (EK) was missing.
The researcher believes that the reason for the absent information is a flaw in how web browsers treat iframes without a “source” attribute placed inside DIV elements. Without the attribute, the iframe does not load anything from a remote location.
Klijnsma explains that most browsers check the content of an iframe as a separate page in its own context. However, in a second stage, a form with hidden input is generated.
“This form is put in the body of the iframe context after which they submit the form. When they submit the form they are sending it from within the iframe context which does not have an actual page loaded which causes the request coming from it to not have a referer,” he says in a blog post.
The researcher created a proof-of-concept (PoC) code to demonstrate how pages can be requested without a referer. The script was tested last week on the latest versions of Google Chrome, Mozilla Firefox and Internet Explorer and performed without a hitch.
Missing referer on Angler landing page more difficult to explain
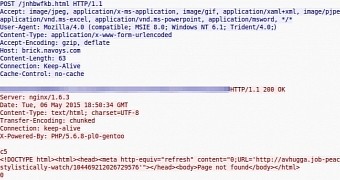
Another problem encountered by the researcher during his analysis of the Angler EK redirects touches on a missing referrer on the landing page for the attack tool.
He says that he could not find an explanation for this behavior, but thinks that it is a browser-related issue touching on how POST requests are performed. He managed to create a PoC that reproduces the problem, but it only works with Internet Explorer.
Regardless of the trick employed, Klijnsma demonstrated how the referer information can be lost at one point in the redirect chain, which is sufficient to cause trouble to security researchers trying to find the path to the malicious advertisement.
 14 DAY TRIAL //
14 DAY TRIAL //