An Android smartphone is delivered to customers with spyware software preloaded, disguised as the Google Play Store app, which cannot be removed because it is integrated into the device’s firmware.
German security software vendor G DATA discovered that N9500 Android devices, built by the Chinese manufacturer Star, are sold with spying capabilities and send personal data to an unknown address in China.
The spyware has full access to all information stored on the phone and, according to G DATA, it can intercept calls, online banking data and text messages, as well as control the camera and the microphone of the device remotely and install new apps.
Christian Geschkat, Product Manager Mobile Solutions at G DATA, says that “the options with this spy program are nearly unlimited. Online criminals have full access to the smartphone.”
All the details are delivered to an anonymous server based in China, and Geschkat notes that “it is not possible to find out who ends up receiving and using the data.”
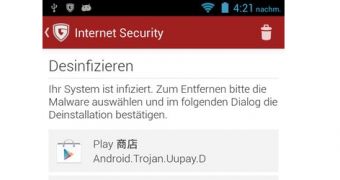
The threat, named Android.Trojan.Uupay.D, runs surreptitiously in the background and, because it is cloaked as the Google Play Store app in the list of running processes, it appears as a legitimate entry.
Since it is embedded in the firmware, the threat cannot be removed, but using an antivirus for the Android platform could show if the device is compromised.
“Unfortunately, removing the Trojan is not possible as it is part of the device's firmware and apps that fall into this category cannot be deleted. This includes the fake Google Play store app of the N9500,” Geschkat noted.
Users unaware of the threat could easily become victims of the cybercrooks, especially since the mobile phone's price is very low (between 130 EUR/$176 and 165 EUR/$223) compared to the hardware specifications.
It runs on a quad-core processor with 1Gb of RAM and is equipped with an 8MP dual camera. Some versions of the device have dual-SIM support. Another incentive is the fact that it looks like a Galaxy S4 from Samsung.
This is not the first reporting of Uupay malware, as Kaspersky also analyzed the piece this year, at the end of March.
The modus operandi was the same in that case, but the name of the installation was DataService and came from a company called Goohi that offered an application pre-installation service for the Android platform using a specific device called “Datang fairy artifact.”
It could be possible that the spyware in Star N9500 was added through the same method.
 14 DAY TRIAL //
14 DAY TRIAL //