Security researchers warn that the Android advertising SDK from InMobi is leveraged by cybercriminals to distribute a piece of scareware.
Bitdefender experts have uncovered several legitimate applications that include the advertising SDK in question, including an older version of the Brightest Flashlight Free app hosted on Google Play.
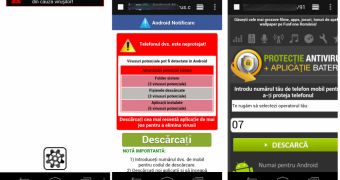
The attack starts with a pop-up ad delivered by the SDK. The pop-up informs users that their devices are infected with malware, and urges them to purchase a so-called disinfection tool.
Users who accept to purchase the disinfection tool are presented with a screen where they’re instructed to enter their mobile phone number. By doing so, they’re actually signing up for a premium-rate mobile service that charges them a certain amount of money for receiving ringtones and wallpapers.
Interestingly, the scam is designed to target users from several countries. Depending on the victim’s location, the bogus malware warning message is written in their own language, and the premium rate service is one that’s available in the user’s country.
In case you’re a victim of such a scam, experts recommend that you immediately unsubscribe from the premium mobile service. Instructions on how to do so should be found in the Terms and Conditions section of the service provider's site.
Also, uninstall all the applications you’ve recently installed, and scan your device with a legitimate antivirus solution for Android.
If you want to make sure that the Android apps you’ve installed don’t invade your privacy, you can use a tool such as Bitdefender Clueful.
According to Bitdefender, InMobi is probably not aware of the fact that cybercriminals are abusing its advertising module to deliver a malicious banner. The most likely scenario is that the ad reached the market by accident.
 14 DAY TRIAL //
14 DAY TRIAL //