Malware did not appear out of nowhere and there is clear information about who wrote the first virus and when. However, since that time back in 1986, malicious software has evolved into something few dared to imagine.
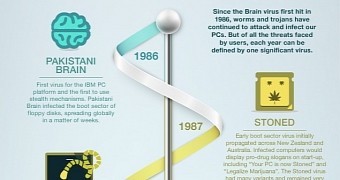
The first computer virus is called Brain and it comes from Pakistan. It infected the boot sector of floppy disks.
First malware was just for fun, or research
Believe it or not, its code contained the names, full addresses and contact details of its creators. Even more unbelievable is that it did not spread through a network of computers, but it traveled by bus, car, bicycle, airplane or whatever transportation people carrying floppies would use.
Brain was not created for damage, but “to explore the security holes of the operating system,” one of its writers, Amjad Farooq Alvi, said in an interview to Mikko Hypponnen in 2011.
The next year, another notable virus appeared, called Stoned. Its origin is New Zealand and no harm would be caused to the computer; instead, one in eight times, the computer screen would display: “Your PC is now Stoned!”
In a malware evolution chart created by ESET, the first destructive malicious software is Morris Worm, which started as a project to count the computers connected to the Internet; however, it all backfired on its creator because of a bug that made the worm continuously self-replicate from an infected computer to all other connected machines. The result was a huge amount of traffic, with significant impact on the Internet of those days.
Malicious activity begins
More destructive pieces were created over the years, which corrupted disks (Disk Killer), gained polymorphic abilities or encrypted parts of the hard disk (One-Half).
Later on, in 1995, the first macro virus popped up, taking advantage of the macro feature in Microsoft Word, which allowed users to record commands that would be executed automatically, as a means to avoid repeating the same task over and over again.
AOL Trojans followed, and then the Melissa worm, which infected Microsoft and Intel networks by sending itself to the first 50 contacts in Outlook email client; its damaging potential consisted in the fact that it was also a macro worm and disabled safeguards in Word documents; moreover, it could also disable mail servers as it increased email traffic.
First mobile worm makes an entrance
The first mobile virus is considered to be Commwarrior, recorded in 2005, which replicated via multimedia messages and Bluetooth and originally targeted phones running Symbian Series 60.
However, Kaspersky talks about Cabir as being the very first mobile malware, discovered in 2004, whose only damage was that it drained the phone battery in a matter of hours.
None of these had a financial purpose behind, and did not take advantage of information from the victim’s computers.
Botnets are created
Storm Worm was a milestone in the evolution of malware because it enslaved computers into a botnet. It was discovered in 2007 and it took advantage of the peer-to-peer protocol for the communication between the infected machines; this would create a problem killing the command and control server because it could change from host to host.
Bruce Schneier said about worms like Storm that they “are written by hackers looking for profit, and they're different. These worms spread more subtly, without making noise;” but Storm did create plenty of noise back in the days, as it infected millions of systems across the world.
Another malware creating a huge botnet was Conficker Worm, identified in 2008. It wreak a lot of havoc in its time, affecting consumers, businesses and government organizations as it would disable several Windows services, slow down connection and lock user accounts.
Malware authors mean serious business
The first military-grade worm came in 2010, taking the form of Stuxnet. Although it infected a small number of computers, it targeted industrial control systems of critical infrastructures.
Believed to be a joint US-Israel project, it caused serious damage at the Natanz nuclear facility in Iran, disrupting the process of uranium enrichment.
Stuxnet is still considered one of the most complex pieces of malware, as it was capable to corrupt the activity of air-gapped systems in a nuclear facility.
ESET’s list of significant malware pieces concludes with four examples created specifically for financial gain or spying: Kelihos (2011), Medre (2012), Hesperbot (2013) and Windigo (2014).
The purpose of their authors is to spread spam, steal AutoCAD documents and exfiltrate sensitive information. In the case of Windigo, more than 25,000 Linux and Unix servers were compromised to direct web visitors to malicious content or to send out spam.
 14 DAY TRIAL //
14 DAY TRIAL //