An independent security researcher tested the links and domains related to About.com and determined that almost all of them were vulnerable to cross-site scripting (XSS) and cross-frame scripting (XFS, iframe injection) attacks.
About.com is one of the largest repositories of expert content intended to answer questions on topics ranging from food, health, money and style to tech, entertainment, careers, parenting and sports. About 100 million users seek information and explanations each month on the portal.
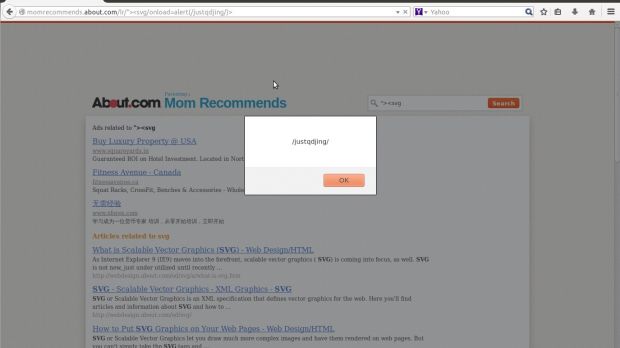
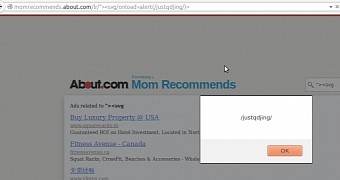
More than 99% of the topic links were found vulnerable
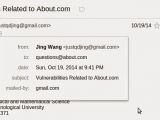
Wang Jing, a PhD student at the Nanyang Technological University in Singapore (Division of Mathematical Sciences - MAS, School of Physical and Mathematical Sciences), created a program he used to check 94,357 links connected to About.com for security flaws.
The result was that “at least 99.875% links of About Group are vulnerable to XSS and Iframe Injection attacks.”
The researcher also found that the search field on the main page could be used in XSS attacks and concluded that all related domains were also plagued by the same weakness.
XSS vulnerabilities are among the most common ones on the web, but they are also the nastiest since exploiting them can lead to stealing information from the user, such as session cookies, log-in data, all by delivering the victim a specially crafted link featuring commands that would allow access to user content in the web browser.
In order to carry out an XFS (iframe injection) attack, information from one domain needs to access resources from a different domain. However, web browsers integrate what is called same-origin policy (SOP), which prevents mixing information with different origins.
As such, unless the web browser has a SOP flaw, such as the recent one reported for Internet Explorer, the XFS attack is unsuccessful.
Proof-of-concept no longer works
Jing said in a blog post on Monday that he reported his findings to About.com on October 19, 2014, but received no answer. He also claims that a fix is yet to be applied.
However, the web browsers the researcher used in his tests (IE 10, Firefox 34 and 36, and Chromium 39) are now outdated.
Testing the proof-of-concepts provided by Jing in IE 11 and the latest versions of Firefox and Google Chrome either generated 404 (page not found) errors or triggered an alert from About.com informing about the malicious attempt, suggesting that the admins already did their job protecting visitors.
A video demonstrating some of the glitches has been posted by the researcher on YouTube:
 14 DAY TRIAL //
14 DAY TRIAL //