Scammers pushing adware to Skype users saw their bots kicked from the network and their operation taken down after a quick analysis of the modus operandi.
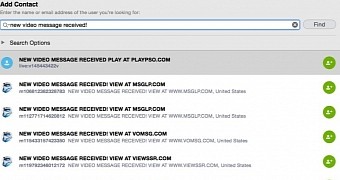
The crooks initiated calls using a name that made the recipient believe that a video message was received. The name also included a link to a malicious domain hosted in the Amazon AWS cloud infrastructure.
Clicking on the URL took the victim to a website asking to install a video player in order to watch the footage.
A hoard of programs get installed
Ronnie Tokazowski found that although a genuine player is added to the system, the installation procedure also includes other programs (some of them dubious in nature), most likely pushed to the user as part of an affiliate program that pays the scammer for each installation.
“Once the executable is opened, it asks to run as administrator. As any user would do…just push play! The user is presented with a screen to install different aspects of the program. Once we are given it the option to start installing, VideoPlayer.exe downloads, installs, and runs many different things. All of these are pieces of adware being installed to the system,” the researcher said in a blog post on Wednesday.
Dismantling the operation
However, Tokazowski took a closer look at the operation and identified the IPs used in the campaign, all part of AWS. A call to Amazon’s security team solved the issue and removed the accounts, breaking the nefarious infrastructure.
By running a partial search of the bot names used by the scammers for abusing Skype users, the researcher found that multiple other domains (a total of 15) were used in the scam.
Again, contacting the owner of the service, Microsoft, solved the problem and the activity from the bad profiles was blocked.
Although this campaign has been stopped, scammers can set up shop at other service providers and register new domains to re-start their business.
 14 DAY TRIAL //
14 DAY TRIAL //