As we have reported in the past several days, these are hard times for LinkedIn. The company has been struggling to warn around 6.5 million of its customers that their passwords have been reset due to an unfortunate data breach.
Cybercriminals see this as a great opportunity to spread their malicious elements and, as a result, spam that leverages LinkedIn’s name and reputation has recorded a considerable growth.
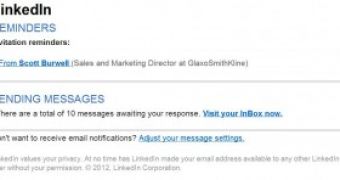
PandaLabs reports that the latest series of ill-intended messages that purport to come from the social media website try to convince recipients to click on links that point to shady websites.
The emails Panda experts have analyzed alert the user on the fact that there are 10 unread messages in his/her LinkedIn inbox and, to make everything even more legitimate-looking, invitation reminders are also contained within the notifications.
However, a closer look reveals that the email is actually sent to around 100 users and the links don’t lead to the genuine website, but to a domain that hosts “a mixed flavor of Adobe and Java exploits,” most likely contained in the infamous Blackhole.
LinkedIn spam is not new, but, after the data breach, fraudsters have begun sending more unsolicited mail, probably thinking that chances for someone to click on the links are higher than before.
Users are advised not only to stay clear of shady-looking notifications, but also, even more importantly, they should always ensure that critical components such as plug-ins, add-ons, Flash Player, Java and Adobe Reader are permanently kept up to date.
Furthermore, experts recommend the use of alternative solutions, some of which may not contain as many security holes as the more popular applications.
Finally, while many security professionals claim that signature-based antivirus solutions are not as effective as they should be, it’s important to keep in mind that modern software uses many technologies that can detect signs of malware based on other factors.
 14 DAY TRIAL //
14 DAY TRIAL //