Adobe rolled out Flash Player 16.0.0.287, an update outside the regular release cycle, indicating that it brings to the table critical security fixes.
On Wednesday, security researcher Kafeine discovered that an instance of Angler included an exploit for an unpatched vulnerability in the then newest version of Flash Player, 16.0.0.257.
Adobe had the new build prepared since last week
Initially, Kafeine revealed partial test results showing that the web-based attack tool delivered the exploit only to some Windows systems running Internet Explorer: XP with IE 6 through 8, Windows 7 with IE 8, and Windows 8 with IE 10.
At that time, the security researcher kept some information private so that cybercriminals would not take action and fix a decision tree error that prevented the attack on Firefox.
The current release of Flash Player (16.0.0.287) is not accompanied by any information from the developer at the moment and many speculate that it addresses the zero-day vulnerability exploited by Angler.
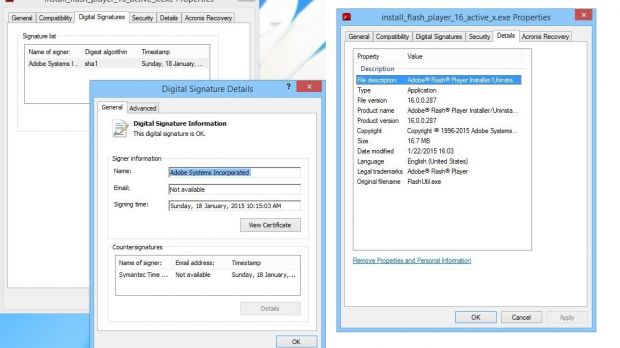
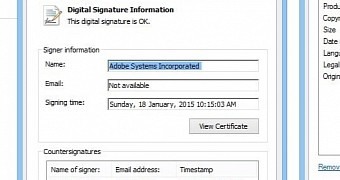
The digital signature for the executable is Sunday, January 18, 2015, a few days before Kafeine broke the news about the new attack method in Angler exploit kit.
Considering that a new build is not signed immediately after it is created, due to testing, it is safe to assume that the executable was created earlier than Sunday and that it addresses a different vulnerability than the one Angler EK takes advantage of.
Disabling Flash Player is a good solution at the moment
In an update posted today, Kafeine added results from more tests as cybercriminals repaired the error that prevented exploiting Flash Player in all browser and Windows versions. He included Firefox and the most recent Flash Player version.
“Any version of Internet Explorer or Firefox with any version of Windows will get owned if Flash up to 16.0.0.287 (included) is installed and enabled,” he wrote.
As such, the only major web browser that is not affected is Google Chrome, most likely because of the sandbox component, which adds an extra layer of security by isolating activity in each tab, thus preventing malware from reaching the computer system.
We contacted Adobe for details about the changes added in Flash Player 16.0.0.287, but we are yet to receive a reply.
As a precaution, the researcher advises users to disable Flash Player until Adobe releases a patch for the issue.
[UPDATE]: An Adobe representative replied to our request for comments saying that the new Flash Player release patches against a different vulnerability (CVE-2015-0310) exploited in the wild. This one is also leveraged by Angler.
The spokesperson informed us that investigation is ongoing in reference to a separate exploit currently available in the wild, which affects Flash Player 16.0.0.287 and earlier.
 14 DAY TRIAL //
14 DAY TRIAL //