Earlier this month we learned from cybercrime investigation company Group-IB that cybercriminals were selling an Adobe Reader X/XI zero-day for prices ranging between $30,000 (€23,000) and $50,000 (€39,000). Adobe still hasn’t managed to address the issue.
The company’s representatives have told TNW that they’re still in the process of determining if this is really a vulnerability and a sandbox bypass. However, they haven’t received a proof-of-concept or a sample from Group-IB, making the task almost impossible to accomplish.
“To this day, we have not yet received a Proof-of-Concept/sample. Without it, there is nothing we can do, unfortunately—beyond continuing to monitor the threat landscape and working with our partners in the security community, as always. We will update you as soon as we have new information and a determination can be made,” Adobe representatives said.
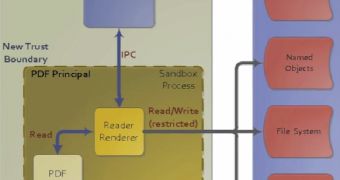
In the meantime, security researcher Kris Kaspersky has also published a video explaining the security hole that apparently “lies in a use-after-free bug when the sandbox process communicates with the reader broker process.”
However, he has also failed to provide Adobe with the details needed to address the issue.
In the meantime, while this is all sorted out, experts from Trend Micro provide some advice on how users can protect themselves against attacks that rely on this exploit.
 14 DAY TRIAL //
14 DAY TRIAL //