A Trojan designed for distributed denial-of-service (DDoS) functionality and aimed at Linux systems has increased its activity during the month of May, researchers warn.
The botnet it creates has been dubbed BillGates by security researchers, initially based on the names seen in some of the variables included in different modules of the malware package.
Botnet is not new
Later, a new version of the Trojan was spotted bearing this name, after two modules it integrated, Bill (filename is “cupsddh”) and Gates (a dropper with the file name “cupsdd”). These modules are detected by Kaspersky as Ganiw. The other tools in the Trojan are identified as Mayday.
The first signs of the BillGates botnet were found in 2014, and apart from a complex modular architecture that is not regularly seen in malware for Linux, an interesting find was the ability to carry out DNS amplification attacks on the targets.
Chinese IP addresses observed in the traffic
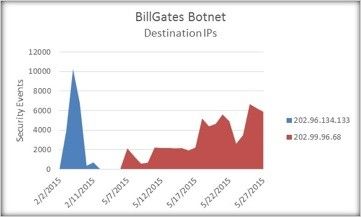
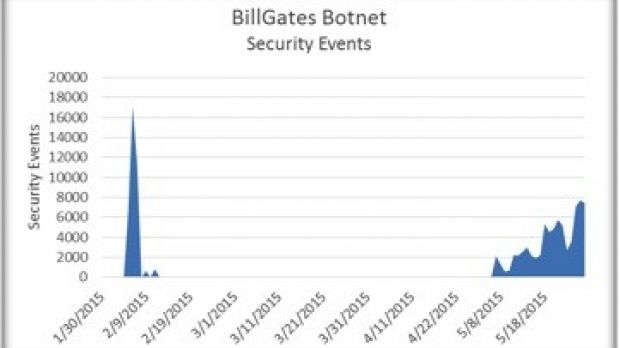
In late February - early May this year, threat researchers at IBM Managed Security Services noticed a spike in BillGates’ activity, with a number of incidents getting closer to the 18,000 mark.
The traffic from the infected systems then died down, until early May, when increased action was again registered, the amount of incidents peaking at almost 8,000.
Researchers say that much of the recently observed traffic was for DNS distributed denial-of-service (DDoS) attacks with packet forgery.
“The threat actors behind the BillGates botnet are not known. However, the destination IP associated with the majority of the traffic observed in May 2015 is 202.99.96.68. This IP’s country of origin is China, which has been found to be associated with the BillGates botnet. Similarly, the majority of the traffic observed in February was also linked with another IP in China, 202.96.134.133,” IBM experts said.
The recommendation for organizations is to use antivirus solutions adapted for the type of device they protect (desktop, server, gateway). On the same note, software products should always be up-to-date.
 14 DAY TRIAL //
14 DAY TRIAL //