It’s nothing short of common practice for rogue antivirus to copy the brands and elements of visual identity of legitimate security products in order to masquerade as genuine products. The latest example was highlighted by the Microsoft Malware Protection Center, and involves an old fake antivirus: Rogue:Win32/FakeXPA.
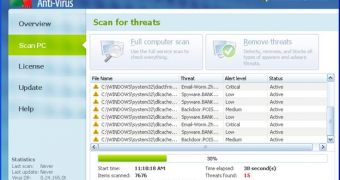
According to David Wood, from MMPC, Rogue:Win32/FakeXPA now goes by as Rogue:Win32/FakeXPA, and as users can see in the image at the top of this article, attackers went as far as copying the actual logo for AVG.
“This is not to be confused with the legitimate antivirus product from AVG – we’ve reached out to AVG, and they are aware the rogue is using their brand.
“FakeXPA's developers are hoping you will confuse it with the real AVG though, as they've even gone to the extent of borrowing AVG's logo for their own user interface.
“The change of name and user interface caused us to examine this variant’s behavior in more detail, and update the description in our malware encyclopedia accordingly,” Wood revealed.
FakeXPA as AVG Antivirus 2011 bombard users with a range of notifications, dialogs, popups, and balloons trying to convince them that their machine is infected with malware.
Of course, the rogue antivirus will only remove the inexistent malicious code once users are tricked into paying for a useless license.
This is another example of social engineering techniques associated with rogue AVs, designed to fool victims into parting with their cash for peace of mind, because the fake AV offers no protection whatsoever.
In addition to relentlessly nagging users with threats of inexistent malware infections, FakeXPA also cripples their browsing experience in Windows.
“It creates a registry entry to set iesafemode.exe as the debugger for a number of common web browsers, including Internet Explorer, Firefox, Opera, Chrome, and Safari. This registry entry is normally used by software debuggers,” Wood added.
“When a user attempts to launch any of these browsers, a copy of the malware will be run instead. Renaming the browser’s executable and running this instead allows it to be launched without interference from the malware.”
For example, attempting to launch Internet Explorer gets FakeXPA to launch its own version of the browser, one that’s apparently running in Emergency Mode.
Users that attempt to visit legitimate sites belonging to security solution providers will find that the URLs are blocked by the malware which tries to prevent consumers from removing it.
 14 DAY TRIAL //
14 DAY TRIAL //