Kaspersky specialists have come across a new version of the Mac OS X MaControl backdoor, which is designed to allow attackers to steal files and run commands on infected computers. The threat has been seen as part of an Advanced Persistent Threat (APT) campaign that targets Uyghur activists.
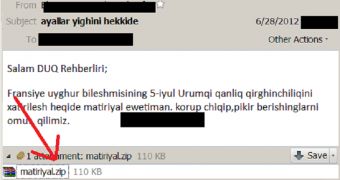
It all starts with an email that contains an archive. When uncompressed, the .zip file reveals a .jpeg picture and a Mac OS X app.
The program actually hides the previously unseen version of the malware, identified in this case as Backdoor.OSX.MaControl.b.
Once it’s executed, it attempts to connect to the command and control server from which it gets further instructions.
“The backdoor is quite flexible – its Command and Control servers are stored in a configuration block which has been appended at the end of the file, which his 0x214 bytes in size. The configuration block is obfuscated with a simple ‘substract 8’ operation,” Costin Raiu explained.
Experts believe that as the popularity of Apple devices grows so will the number of such APTs.
 14 DAY TRIAL //
14 DAY TRIAL //