The website for AOL Search can be used by a threat actor in what is called a reflected file download (RFD) attack, to trick an unsuspecting user into downloading a malicious file on the computer, a security researcher has found.
The vulnerability uncovered on AOL’s domain was presented by Oren Hafif, of Trustwave security company, at the 2014 edition of the Black Hat Europe security conference in Amsterdam.
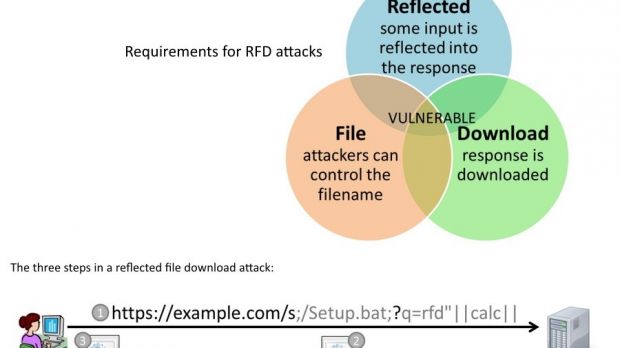
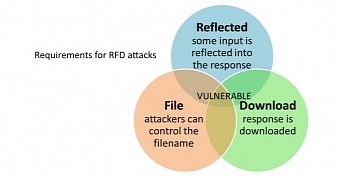
Reflected file download attack
It consists in sending the victim a maliciously crafted link to an executable file (CMD, BAT) that appears to be hosted on a trusted domain. However, the file is not available from the trusted domain and its content, which is made of commands or script files, is actually included in the link itself.
When the link is accessed, the response from the web browser is a download for a file that is in fact created on-the-fly with the information in the URL.
The attack does not work on Google Chrome because the developer implemented a fix for the vulnerability, as pointed out by Hafif in a blog post at the end of October 2014.
Proof-of-concept shows the flaw on AOL's domain
Ricardo Iramar dos Santos, a security engineer from HP, has found that the RFD glitch is present on AOL’s domain, allowing an attacker to deliver a malicious file to a victim.
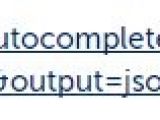
He provided the following proof-of-concept that demonstrates the flaw in Internet Explorer and Mozilla Firefox:
The result is serving a batch file with instructions to deploy the default Calculator application included in Windows operating system.
He explains that in the search for 'iramar "||calc||' on AOL, the browser encodes the double quotes, but the server escapes them and returns the JavaScript Object Notation (JSON) in the body response. “Since the response has the header "Content-Type: application/x-suggestions+json;charset=UTF-8" the browser will automatically try to download the reflected file,” dos Santos says.
To the user, the entire process looks like a file is offered for download from autocomplete.search.aol.com and it would not raise any suspicions. With some social engineering, an attacker could gain complete control over a victim’s computer system by fooling them into downloading and launching malicious files that appear to originate from a trusted party.
 14 DAY TRIAL //
14 DAY TRIAL //